Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the Splunk: The Basics Room on TryHackMe. In this room we will learn to use Splunk, and how this product, which is one of the leading SIEM solutions in the market, is used by SOC analysts around the world to investigate logs.

Room URL:
https://tryhackme.com/room/splunk101
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Splunk is one of the leading SIEM solutions in the market. It allows users to collect, analyze, and correlate network and machine logs in real time. In this room, we will explore the basics of Splunk and its functionalities, and how it provides better visibility of network activities and helps speed up detection.
This room covers the following learning objectives:
If you are new to SIEM, please complete the Introduction to SIEM room.
Answer: No answer needed
Before proceeding with the following tasks, start the attached virtual machine by clicking the Start Machine below. Start Machine
The machine may take up to 3-5 minutes to start. After the machine starts, the Splunk Instance can be accessed at http://MACHINE_IP either directly on the AttackBox or via the TryHackMe VPN.
Answer: No answer needed
Splunk has three main components: Forwarder, Indexer, and Search Head. These components work together to help us search and analyze the data. These components are explained below:
Splunk Forwarder is a lightweight agent installed on the endpoint intended to be monitored, and its main task is to collect the data and send it to the Splunk instance. It does not affect the endpoint’s performance as it takes a few resources to process. Some of the key data sources are:
The forwarder collects the data from the log sources and sends it to the Splunk Indexer.
Splunk Indexer plays the main role in processing the data it receives from forwarders. It parses and normalizes the data into field-value pairs, categorizes it, and stores the results as events, making the processed data easy to search and analyze. Now, the data, which is normalized and stored by the indexer, can be searched by the Search Head.
Splunk Search Head is the place within the Search & Reporting App where users can search the indexed logs, as shown below. The searches are done using the SPL (Search Processing Language), a powerful query language for searching indexed data. When the user performs a search, the request is sent to the indexer, and the relevant events are returned as field-value pairs..
The Splunk Forwarder is installed on endpoints, which in turn collects data, and afterwards sends it to the Splunk instance.
Answer: Forwarder
When you access Splunk, you will see the default home screen as shown below:

Let’s look at each section of this home screen.
The top panel is the Splunk Bar. In the Splunk Bar, we have the following options available:
The Splunk Bar, allows users to switch between installed Splunk apps instead of using the Apps panel.
Next is the Apps Panel. This panel shows the apps installed for the Splunk instance. The default app for every Splunk installation is Search & Reporting.
You can also switch between the Splunk Apps directly from the Splunk Bar, as shown below, without using the Apps Panel.
The next section is Explore Splunk . This panel contains quick links to add data to the Splunk instance, add new Splunk apps, and access the Splunk documentation.
The last section is the Home Dashboard. By default, no dashboards are displayed. You can choose from a range of dashboards readily available within your Splunk instance. You can select a dashboard from the dropdown menu or by visiting the dashboards listing page.
You can also create dashboards and add them to the Home Dashboard. The dashboards you create can be viewed separately from the other dashboards by clicking on the Yours tab.
Please review the Splunk documentation on Navigating Splunk here.
Make you started up a Splunk machine, and access its IP adress from the AttackBox or your machine on THMs VPN.
Now, press the add data tab and you will see the following menu:
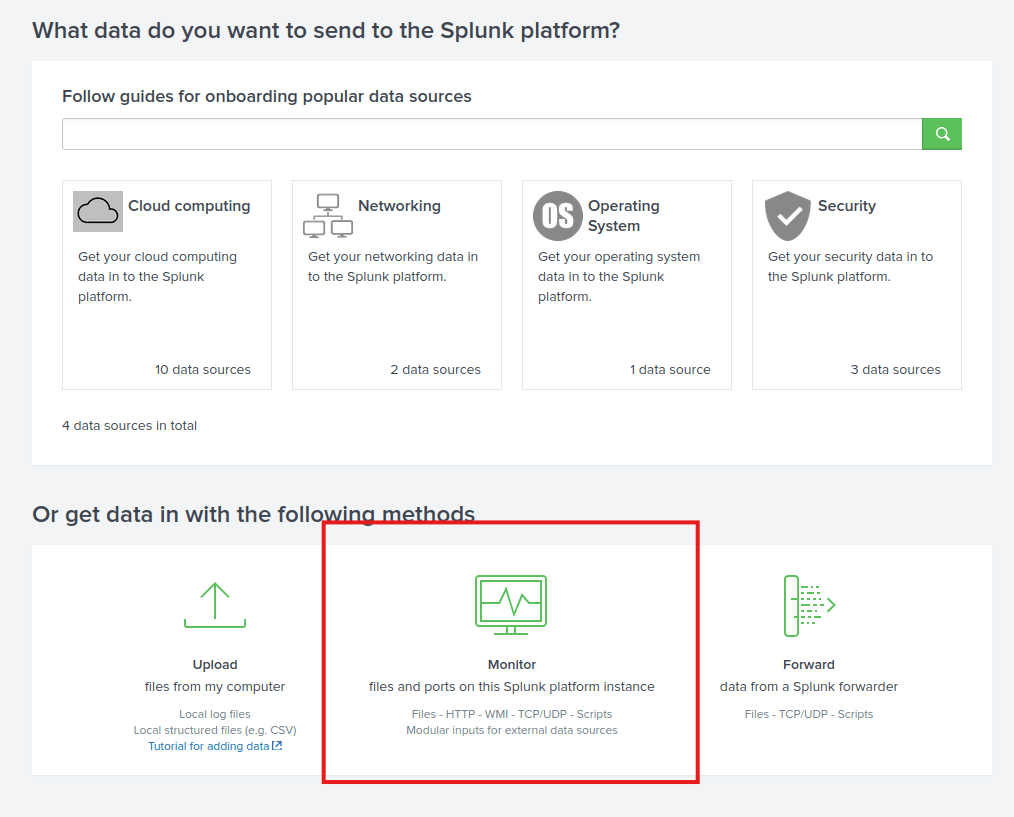
Underneath the monitor option, we see the functionality to collect data from files and ports.
Answer: Monitor
Splunk can ingest any data. According to the Splunk documentation, when data is added to Splunk, the data is processed and transformed into a series of individual events. The data sources can be event logs, website logs, firewall logs, etc. The data sources are grouped into categories.
Below is a chart listing from the Splunk documentation detailing each data source category.
In this task, we’re going to focus on VPN logs. We’re presented with the following screen when we click on the Add Data link on the Splunk home screen.
We will use the Upload Option to upload the data from our local machine.
Download the log file VPN_logs from the Download Task Files button in the room and upload it to the Splunk instance we started in Task #2. If you are using the AttackBox, the log file is available in the /root/Rooms/SplunkBasic/ directory.
To upload the data successfully, you must follow five steps, which are explained below:
Press the upload method button:
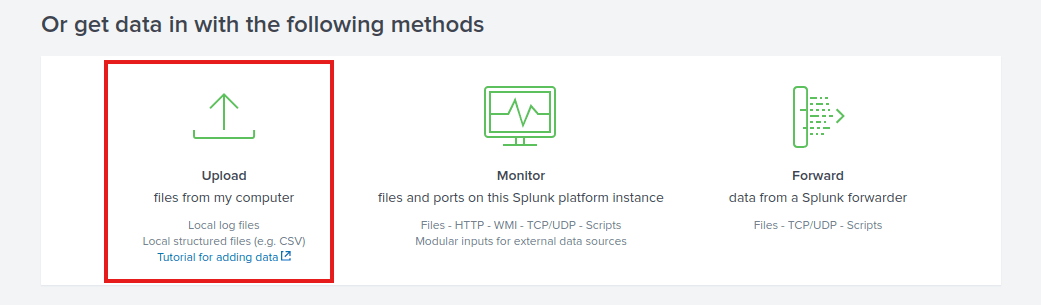
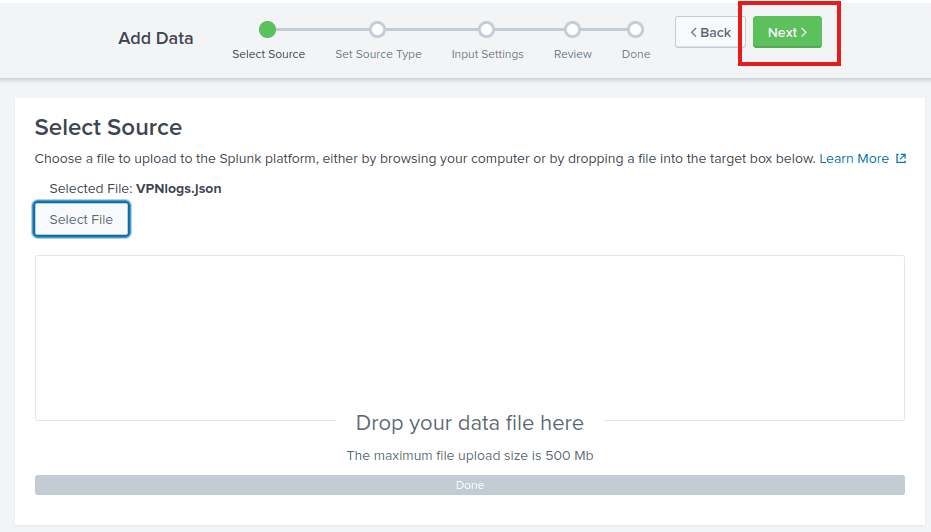
Navigate to the files you downloaded, or find them at /root/Rooms/SplunkBasic/ on the AttackBox.
Now press next:
Now you have to select the source type, which is JSON. Press next again.
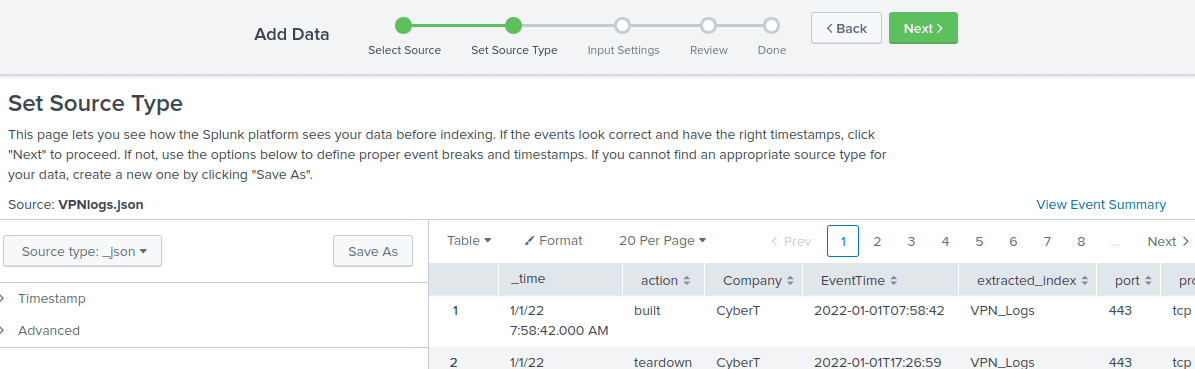
Now we have to enter a host field value, which should be similar to the name of the machine (host). Let’s enter VPN_Connections here.
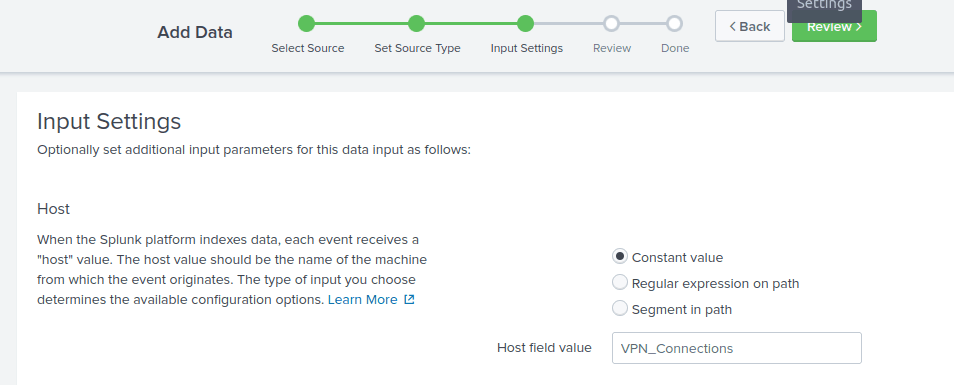
Now, create a new index called VPN_Logs. Press next, check everything and press Submit. Finally, press Start Searching.
Now you come in the search screen. To see the correct number of events I have to press the search button once.
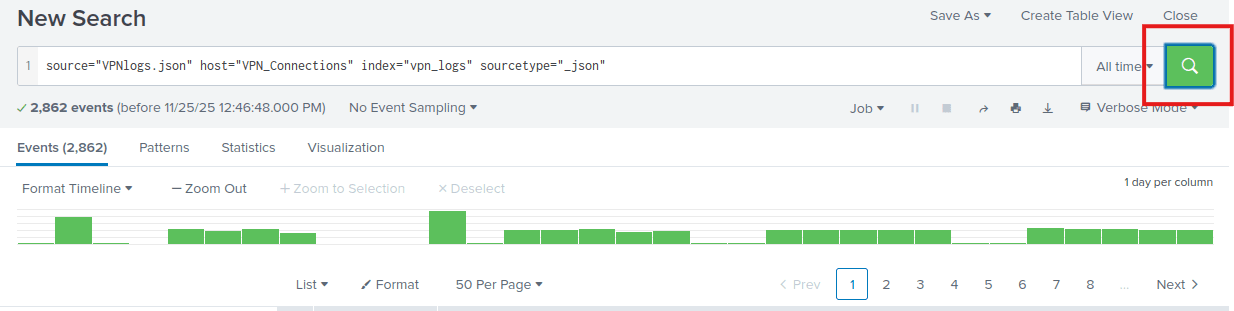
The number of events is 2862.
Answer: 2862
Great job. Now let’s find how many of these events are captured by Maleena. This is not that hard. Find the Username field on the left menu, and press Maleena.
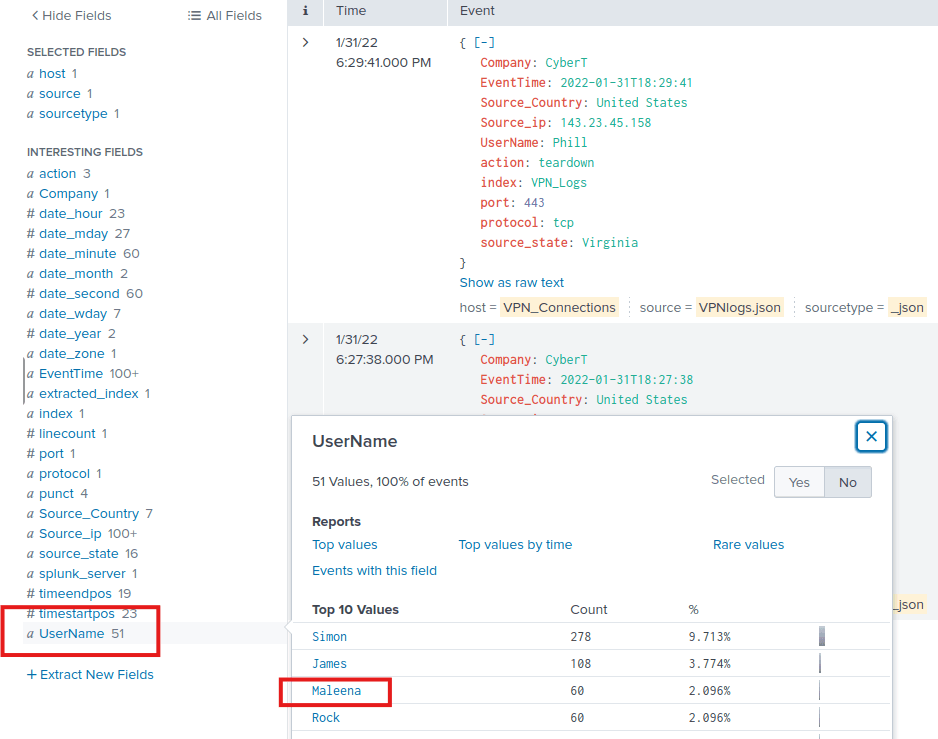
Alternatively, you can enter the following in the search input field:
source=”VPNlogs.json” host=”VPN_Connections” index=”vpn_logs” sourcetype=”_json” UserName=Maleena
60 events should show up.
Answer: 60
If you look at the data rows, you can see that there is a field called Source_ip.
Make sure you removed the filter on Maleena, and press the source ip field. Select any of the IPs to see how to edit the input field. Now you can edit the IP address to sort on.
source=”VPNlogs.json” host=”VPN_Connections” index=”vpn_logs” sourcetype=”_json” Source_ip=”107.14.182.38″
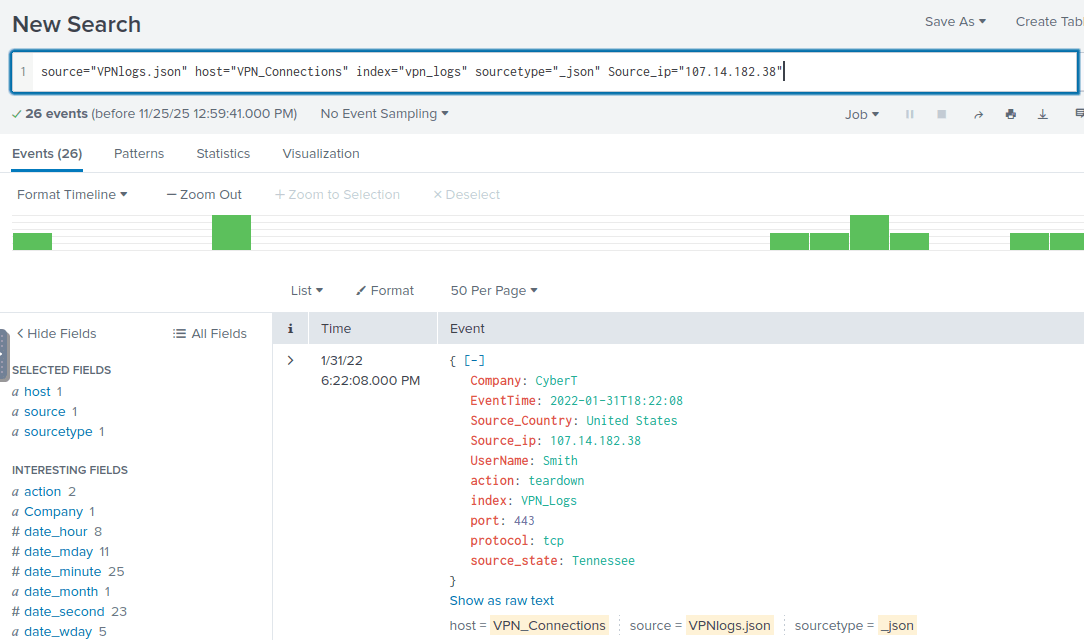
Now you should see that the username associated to this IP address is Smith.
Answer: Smith
The field we need to use here is called Source_Country.
Normally, if we were only interested in France we would use something like “Source_Country=France”, but to do the opposite we !=. The search field should look like this:
source=”VPNlogs.json” host=”VPN_Connections” index=”vpn_logs” sourcetype=”_json” Source_Country!=France
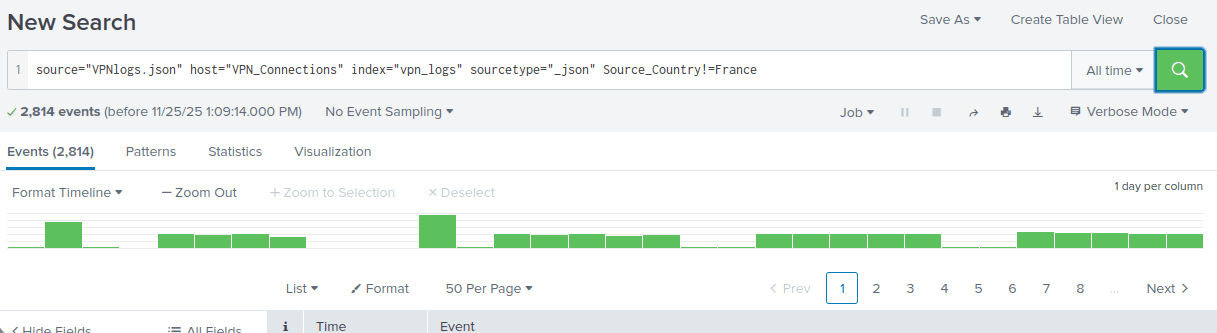
2814 events remain.
Answer: 2814
I hope you are getting the grip of these. You should probably know now how to filter on a specific commands using the Splunk search language (SPL). Simply write:
source=”VPNlogs.json” host=”VPN_Connections” index=”vpn_logs” sourcetype=”_json” Source_ip=”107.3.206.58″
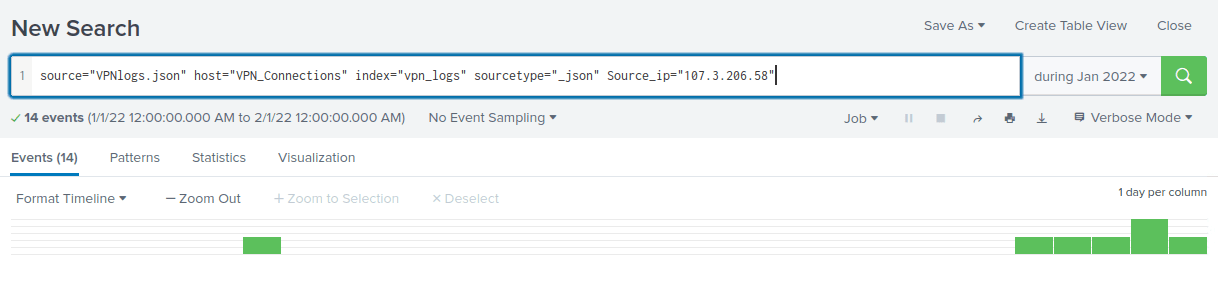
Answer: 14
Well done! In this room, you learned about Splunk’s core components, explored the Splunk interface, and practiced uploading data to Splunk. You have gained the foundational knowledge of Splunk SIEM.
If you’d like to dig deeper, you can explore the following Splunk walkthrough and challenge rooms to understand how Splunk is effectively used in investigating incidents.
Answer: No answer needed.

Congratulations on completing Splunk: The Basics. Splunk is such as big name in the world of SIEMs, and that’s why it was awesome to get an introduction to it. I am not sure how I felt about the final exercises where we had to search for events, without getting an introduction that is.
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other TryHackMe SOC Level 1 Path walkthrougs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] Splunk: The Basics […]