Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the SOC Workbooks and Lookups room on TryHackMe. In this room we will discuss why workbooks exist and how they make the process of triaging alerts easier for SOC analysts.
Room URL:
https://tryhackme.com/room/socworkbookslookups
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Alert triage is a complex process that often requires analysts to gather additional information about affected employees or servers. This room explores SOC workbooks designed to streamline alert triage and explains various lookup methods to quickly retrieve user and system context.
Answer: No answer needed
An alert shows G.Baker logged into the HQ-FINFS-02 server, downloaded a financial report, and shared it with R.Lund. To triage this, analysts must answer:
svc-veeam-06 (backup) or svc-nginx-pp (web app).Raymond is US Financial Adviser 🙂
Answer: US Financial Adviser
Simply look it up in the table. HQ-FINFS-02 stores financial records.
Answer: financial records
Yea! This looks legit. R.Lund requires this kind of materials for his jobs, and the financial records are indeed stores on the server he accessed. False positive.
Answer: yea
Firewall logs show suspicious activity:
103.61.240.174 connects to firewall on TCP/10443.10.10.0.53.172.16.15.0/24 (Database subnet), no open ports found.172.16.23.0/24 (Office subnet), attack continues.10.10.0.0/16172.16.15.0/24172.16.23.0/24103.61.240.174 performs VPN brute force against vpn.tryhatme.thm.10.10.0.53 from the VPN subnet.Network diagrams allow SOC analysts to:
Port 10443 is commonly used for SSL VPN connections, often as an alternative to the default port 443 to avoid conflicts with the web interface or to circumvent port blocking. This port is also seen on the network diagram as is listed as VPN.
Answer: VPN
The database subnet is listed as 172.16.15.0/24. So this means the IP 172.16.15.99 is part of that subnet. This is the database subnet.
Answer: database subnet
This is definitely sounds like a true positive. The attacker brute forced a VPN and is actively scanning for vulnerabilities in the other subnets. Dangerous!
Answer: TP
SOC workbooks provide a step‑by‑step guide that ensures analysts don’t skip critical steps. By following them, L1 analysts can deliver consistent, high‑quality triage and avoid premature or incorrect verdicts.
Workbooks outline the steps analysts must follow. This makes them perfect for relatively inexperienced analysts, commonly called SOC L1 Analysts.
Answer: SOC L1 Analyst
The purpose of gathering information about the users, hosts and other relevant data is called enrichment.
Answer: Enrichment
The workbook example on THM shows that the expected user’s location is found in BambooHR.
Answer: BambooHR
Different teams have different approaches to workbook building. Some teams may have hundreds of complex workbooks for every possible detection rule, more like a SOAR automation playbook than human guides. Other teams may prepare just a few high-level workbooks for the most common attack vectors and rely more on the experience and decision-making of L1 analysts. In any case, you as an L1 analyst should know how to divide your investigation into modular blocks and build simple workbooks around it.
View Site
Let’s practice building the workbooks! Open the attached site by pressing the View Site button and fill in the missing workbook steps from the options. Drag and drop the options to their respective positions. If the position is correct, the option will stick there. Once you are done, receive the flag and continue to the next section!
We need to put 6 out of 8 boxes into the right location on each workbook. I will post a screenshot of each workbook, and explain shortly the decisions made.
Make sure the first workbook looks like this (apologies for the dark picture, as I had to hide the flag message but the background is still darkened):
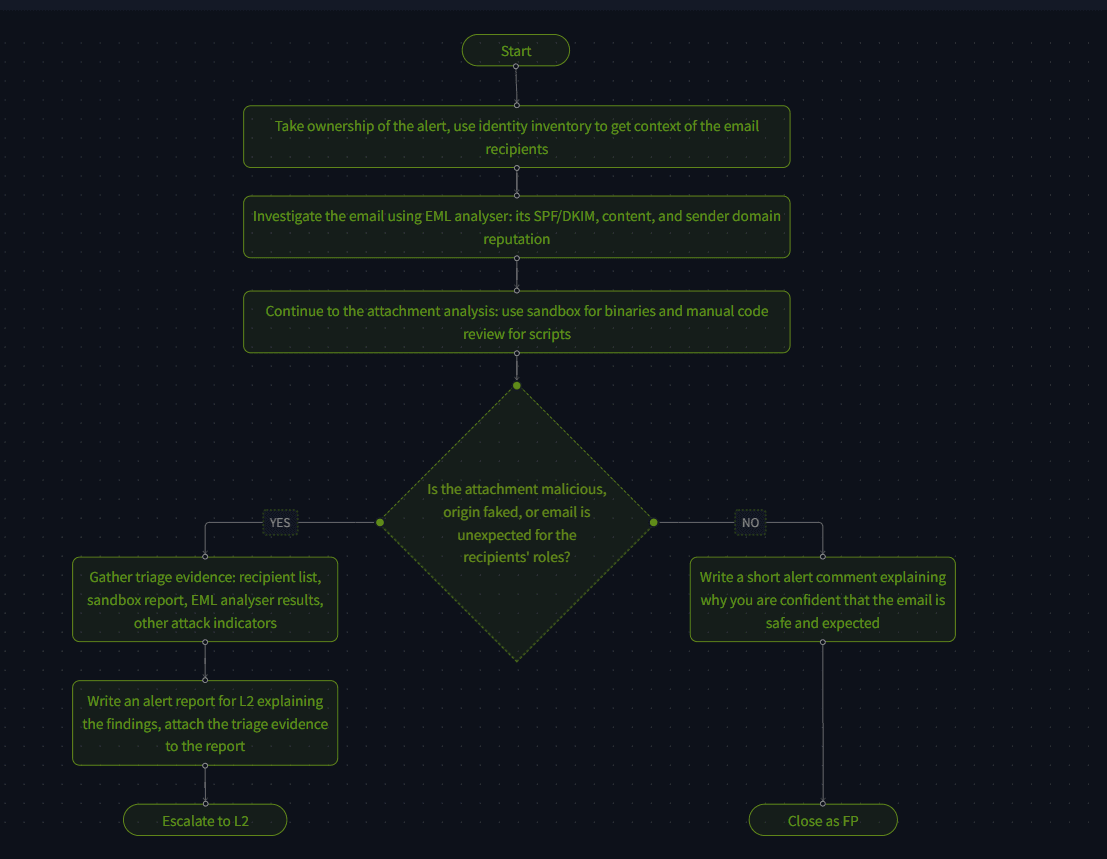
The first 3 steps all are about taking ownership, and gathering all the relevant information. Then we either conclude the email is safe and we close it as FP, or we gather triage evidence and escalate to L2 with a summary of your findings.
Answer: THM{the_most_common_soc_workbook}
Your workbook should look like this:
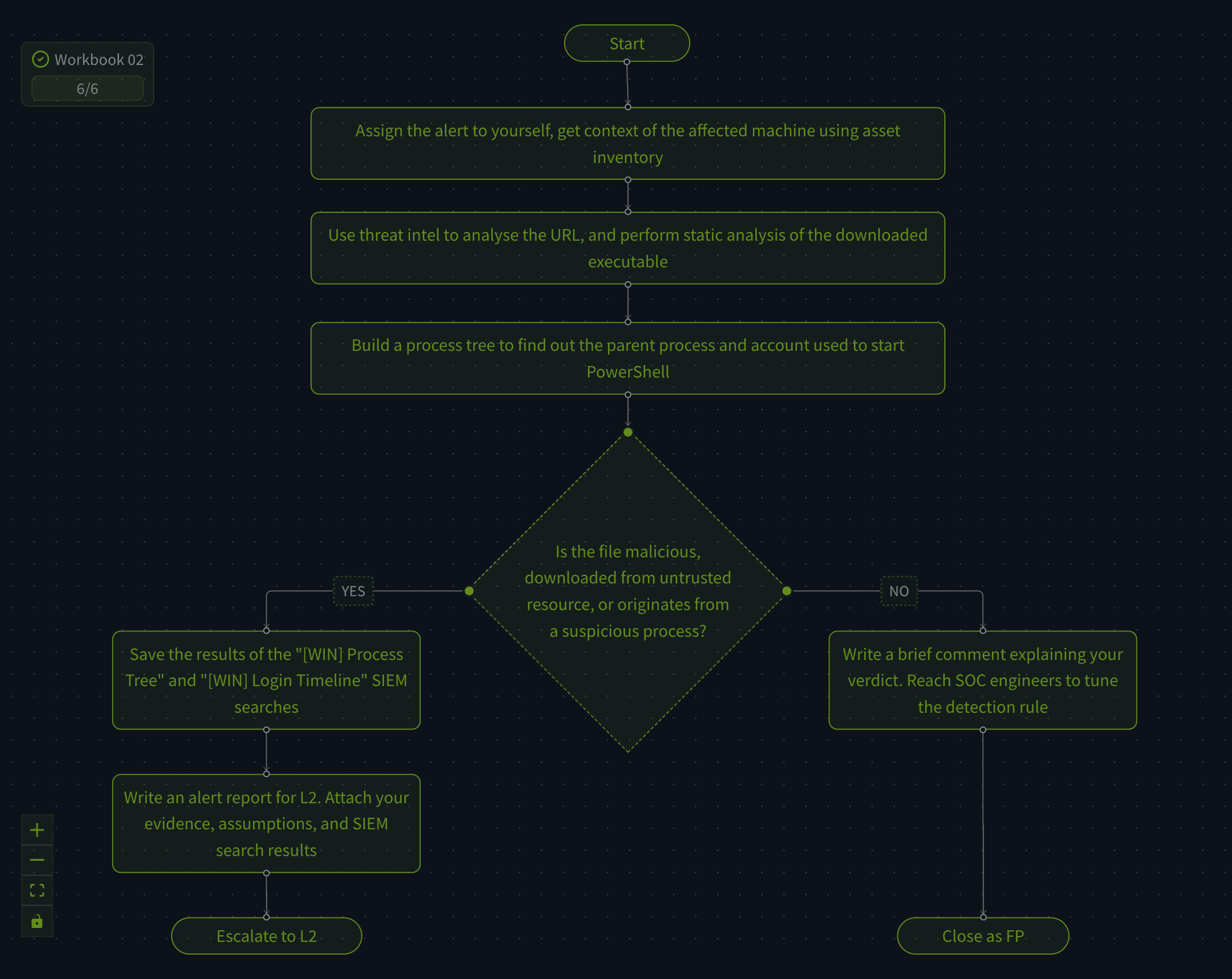
Again, first we assign the alert to ourselves, and afterwards we collect information. Finally, we either conclude it is a false positive, or write a alert report for L2 and assign it to them with all evidence.
Answer: THM{be_vigilant_with_powershell}
Here is the complete third workbook:
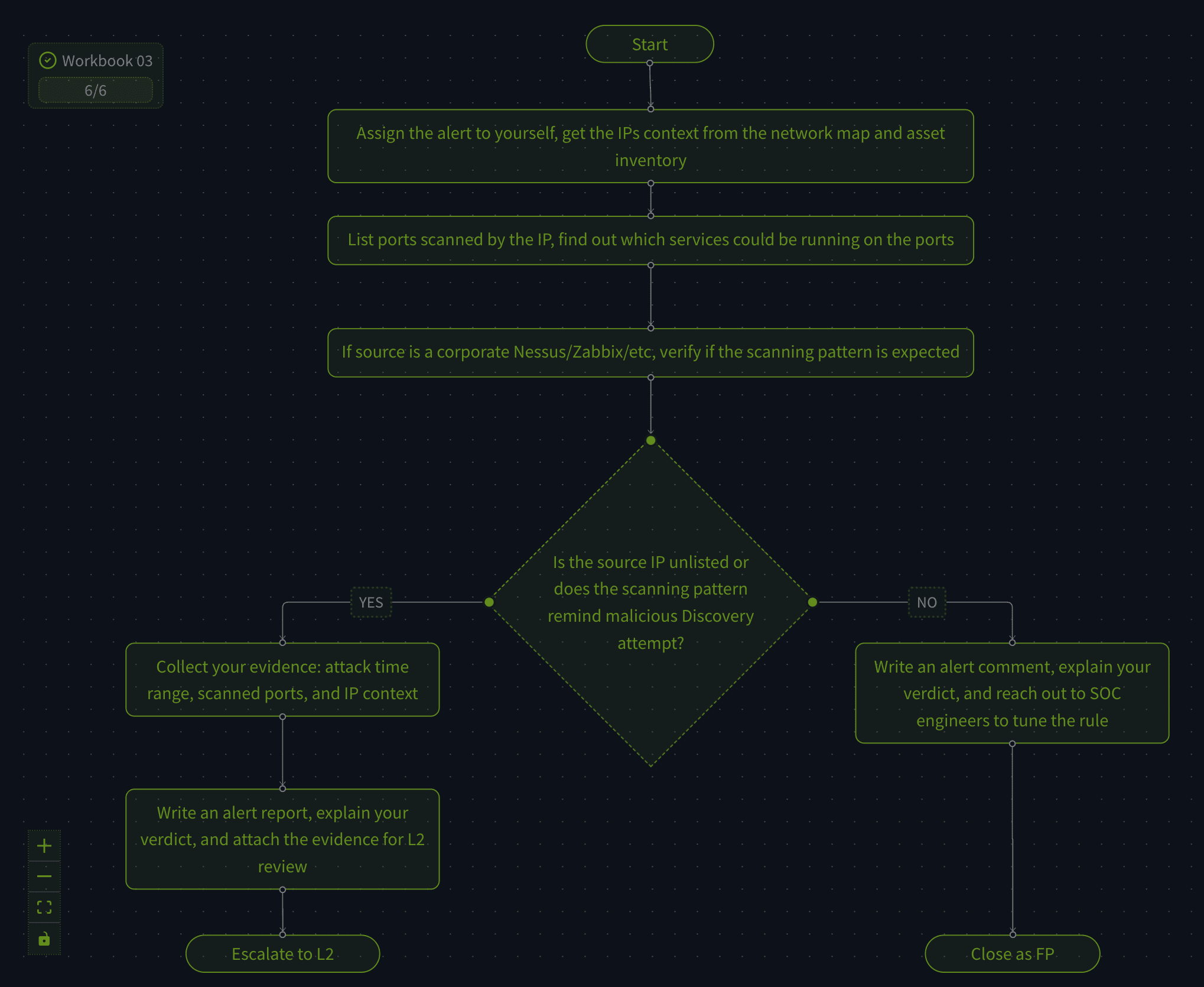
I hope you get this now. We assign the alert, collect information, and either reach a FP verdict (and get the rules tuned) or collect evidence and send it to L2.
Answer: THM{asset_inventory_is_essential}
Nice work on building the workbooks! Remember to use the existing lookups like asset inventory or network map to better understand the alerts, and push your team to implement and maintain workbooks to streamline and simplify SOC operations. Hope you enjoyed the room!
Answer: No answer needed.

Congratulations on completing SOC Workbooks and Lookups! I hope you realise that while being a SOC Analyst can be difficult, there are a lot of processes and tools to help make our lives easier. Workbooks are a big part of it!
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other TryHackMe SOC Level 1 Path walkthroughs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] SOC Workbooks and Lookups […]