Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the Introduction to Phishing scenario of the SOC Simulator on TryHackMe. In this scenario we learn to use the SOC Simulator by completing our first scenario. Close all True Positive alerts to pass!
Room URL:
https://tryhackme.com/soc-sim/scenarios?scenario=introduction-to-phishing
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Go to the URL of the scenario and press start. You will now be asked to choose a SIEM tool.
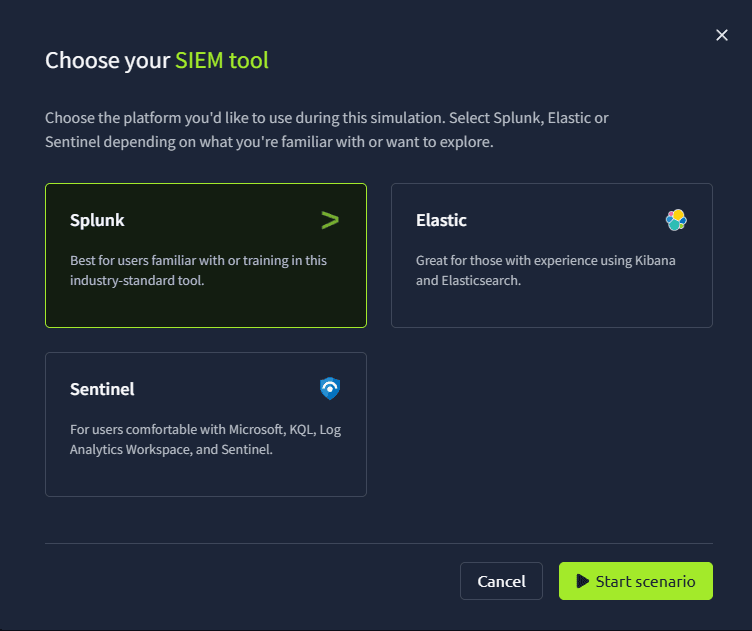
It does not really matter what to pick here, but pick any which sound great. The difference between the two systems is as follows: Splunk is a commercial, proprietary platform often favored for its ease of use and powerful, out-of-the-box SIEM capabilities, while the Elastic Stack is an open-source solution that is more customizable and cost-effective for those willing to manage it themselves. Finally, Sentinel is very focused on Microsoft! Anways, I will pick Splunk for now.
Press start scenario and the scenario will load, which will take a few minutes.
To complete a Scenario, find all the True Positive alerts. Keep triaging alerts until you’ve closed them all! You will be met by a dashboard.We find the alerts in the alert queue.
Open it through the menu on your left:
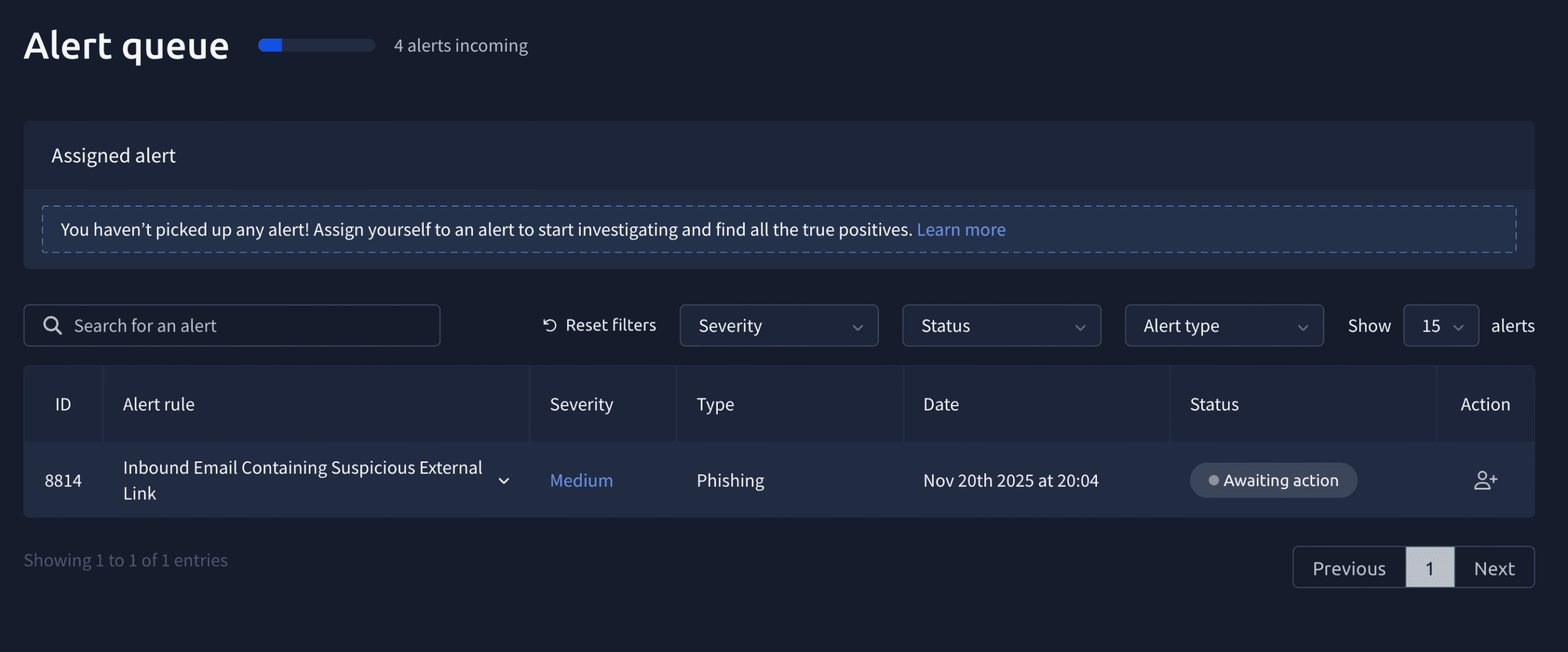
There is 1 alert waiting on us, but four more are on their way if you want to wait a bit.
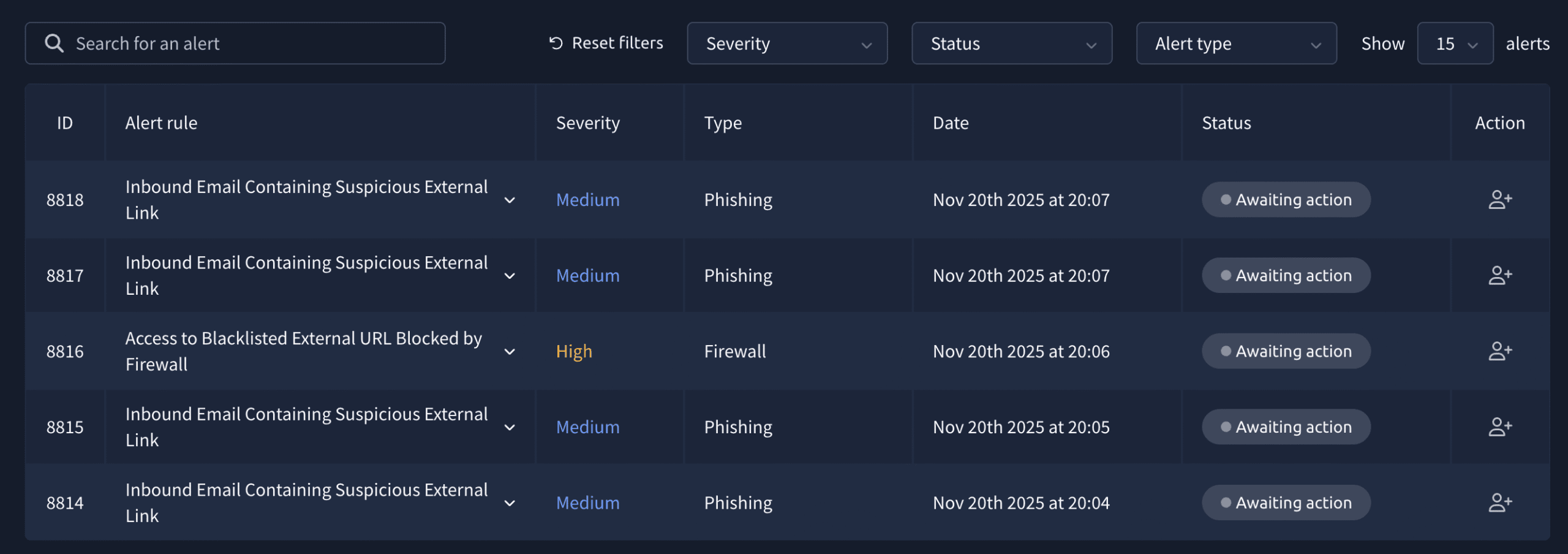
While technically you should start with the highest severity alert, I will cover them in the order they came in. We will start with the first alert, which has ID 8814 and contains the following info:
Description:
This alert was triggered by an inbound email contains one or more external links due to potentially suspicious characteristics. As part of the investigation, check firewall or proxy logs to determine whether any endpoints have attempted to access the URLs in the email and whether those connections were allowed or blocked.
datasource: email
timestamp: 11/20/2025 20:02:00.489
subject: Action Required: Finalize Your Onboarding Profile
sender: onboarding@hrconnex.thm
recipient: j.garcia@thetrydaily.thm
attachment: None
content:
Hi Ms. Garcia,\n\nWelcome to TheTryDaily!\n\nAs part of your onboarding, please complete your final profile setup so we can configure your access.\n\nKindly click the link below:\n\n<a href=”https://hrconnex.thm/onboarding/15400654060/j.garcia”>Set Up My Profile</a>.\n\nIf you have questions, please reach out to the HR Onboarding Team.
Direction: In bound
Go ahead and assign it to yourself by using the Action button to the right. Then it moves to the top of the screen and you are able to write a case report. A screen pops up asking whether you think it is a true positive or false positive.
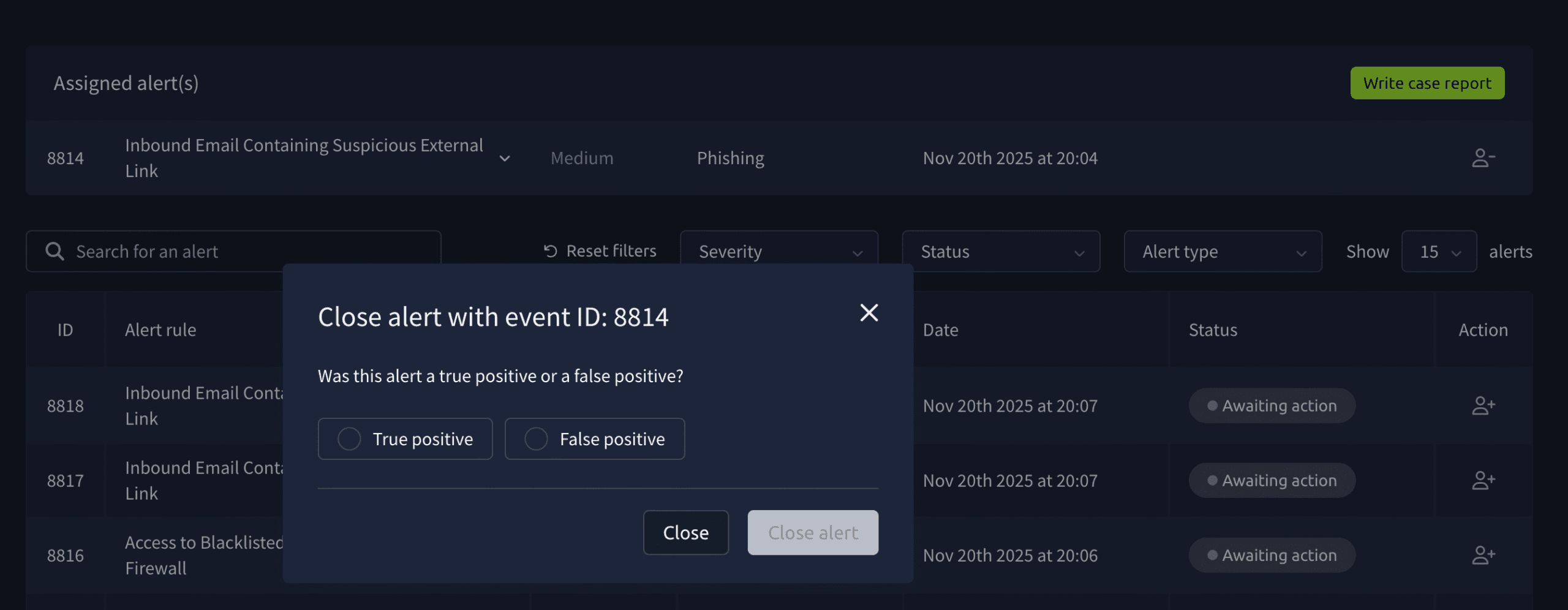
After doing this you get to write an incident report:
But before we move on we need to gather more information.
Usually, emails with links to click on are quite suspicious. We need to check for the domain https://hrconnex.thm in the SIEM to see if the user actually clicked on the link. If you search for the domain in the SIEM you will see an interesting email from HR:
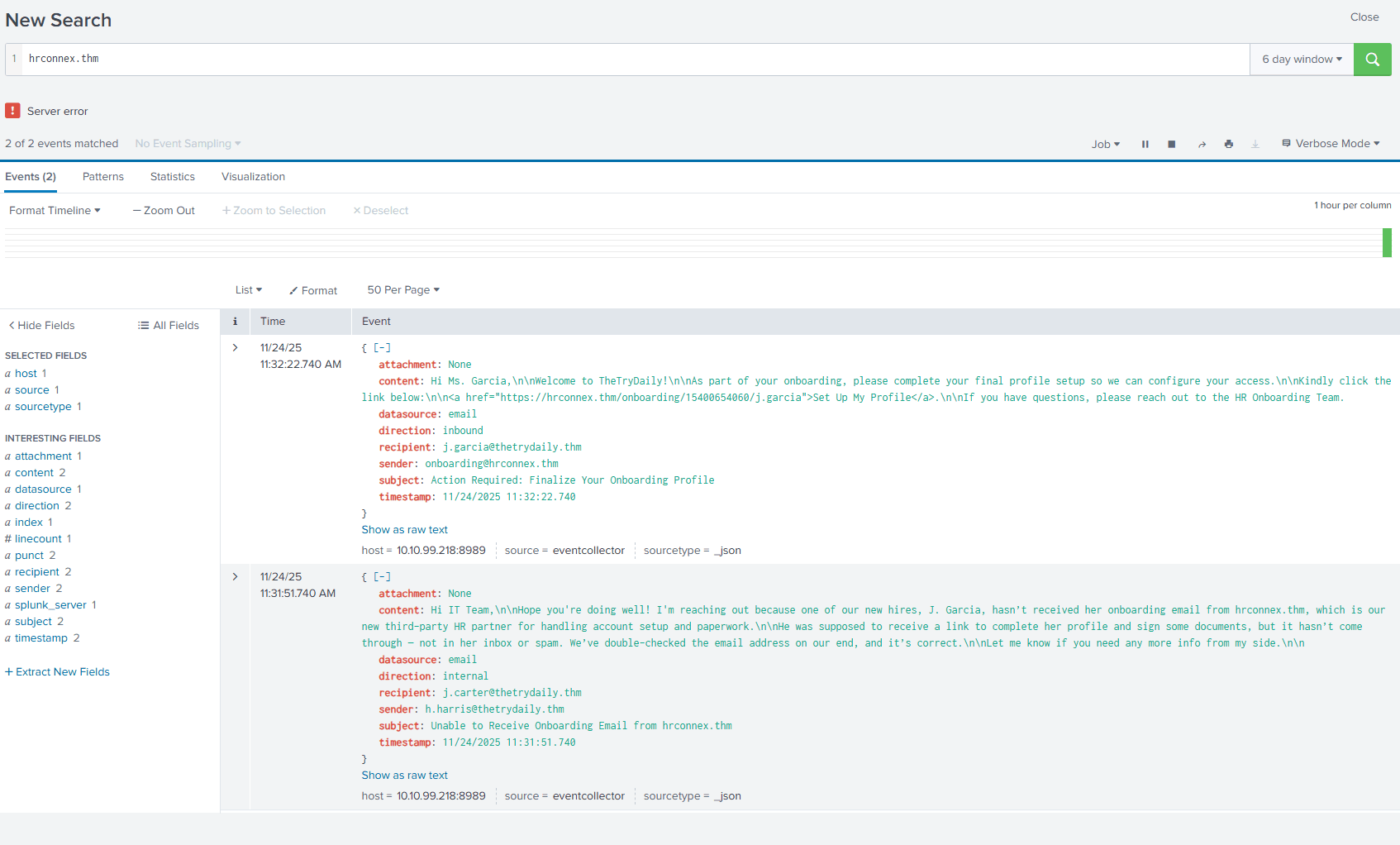
Hi IT Team,\n\nHope you’re doing well! I’m reaching out because one of our new hires, J. Garcia, hasn’t received her onboarding email from hrconnex.thm, which is our new third-party HR partner for handling account setup and paperwork.\n\nHe was supposed to receive a link to complete her profile and sign some documents, but it hasn’t come through — not in her inbox or spam. We’ve double-checked the email address on our end, and it’s correct.\n\nLet me know if you need any more info from my side.\n\n
This seems to contradict our earlier suspicions. The email actually seems to be from a third-party HR partner. I guess it is a false positive. Write the incident report and classify as FP.
Let’s tackle another one:
Description:
This alert was triggered by an inbound email contains one or more external links due to potentially suspicious characteristics. As part of the investigation, check firewall or proxy logs to determine whether any endpoints have attempted to access the URLs in the email and whether those connections were allowed or blocked.
datasource: email
timestamp: 11/20/2025 20:03:09.489
subject: Your Amazon Package Couldn’t Be Delivered – Action Required
sender: urgents@amazon.biz
recipient: h.harris@thetrydaily.thm
attachment: None
content:
Dear Customer,\n\nWe were unable to deliver your package due to an incomplete address.\n\nPlease confirm your shipping information by clicking the link below:\n\nhttp://bit.ly/3sHkX3da12340\n\nIf we don’t hear from you within 48 hours, your package will be returned to sender.\n\nThank you,\n\nAmazon Delivery
direction: inbound
OK, this is quite similar as it is a email with a link to click. But here we have an email from a Amazon look-a-like domain, and the bit.ly shortlink also seems to be very suspicious. If you search the SIEM you can see that the user actually tried to click the link, but fortunately it was blocked:
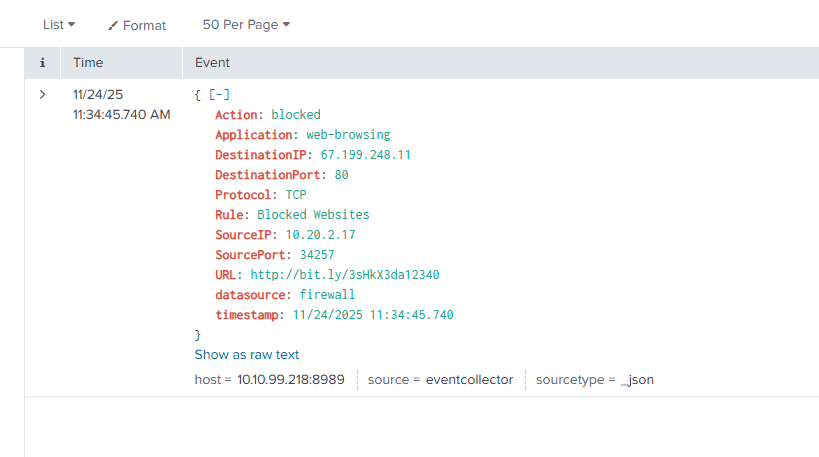
This all points to something suspicious. I will classify it as true positive! We don’t need to escalate as the link got blocked. I filled out the case report as follows:
Time of activity: 11/24/25
List of Affected Entities: –
Reason for Classifying as True Positive: Amazon look-a-like, and suspicious link.
Reason for Escalating the Alert: –
Recommended Remediation Actions: Talk with the user about clicking on phishing emails.
List of Attack Indicators: Is from an unrecognized contact source.
Next one! A high severity one!
Description:
This alert was triggered when a user attempted to access an external URL that is listed in the organization’s blacklist or threat intelligence feeds. The firewall or proxy successfully blocked the outbound request, preventing the connection. Note: The blacklist only covers known threats. It does not guarantee protection against new or unknown malicious domains.
datasource: firewall
timestamp: 11/20/2025 20:04:23.489
Action: blocked
SourceIP: 10.20.2.17
SourcePort: 34257
DestinationIP: 67.199.248.11
DestinationPort: 80
URL: http://bit.ly/3sHkX3da12340
Application: web-browsing
Protocol: TCP
Rule: Blocked Websites
Wait a minute! This is the link we looked at earlier. Luckily it got blocked. But maybe we should escalate it anyway, so that some threat analysts can investigate whether other domains should get blocked.
Description:
This alert was triggered by an inbound email contains one or more external links due to potentially suspicious characteristics. As part of the investigation, check firewall or proxy logs to determine whether any endpoints have attempted to access the URLs in the email and whether those connections were allowed or blocked.
datasource: email
timestamp: 11/20/2025 20:05:27.489
subject: Unusual Sign-In Activity on Your Microsoft Account
sender: no-reply@m1crosoftsupport.co
recipient: c.allen@thetrydaily.thm
attachment: None
content:
Hi C.Allen,\n\nWe detected an unusual sign-in attempt on your Microsoft account.\n\nLocation: Lagos, Nigeria\n\nIP Address: 102.89.222.143\n\nDate: 2025-01-24 06:42\n\nIf this was not you, please secure your account immediately to avoid unauthorized access.\n\n<a href=”https://m1crosoftsupport.co/login”>Review Activity</a>\n\nThank you,\n\nMicrosoft Account Security Team
direction: inbound
Once more a phishing link. This time from a domain that looks a lot like Microsoft: no-reply@m1crosoftsupport.co. In addition, the email tries to panic the reader by writing that their Microsoft account is hacked from someone in Nigeria. Without a doubt a true positive!
Time of activity:
List of Affected Entities:
Reason for Classifying as True Positive: Definitely phishing. Microsoft pretending email and creating false feeling of urgency.
Reason for Escalating the Alert: Yes, domain should get blocked.
Recommended Remediation Actions:
List of Attack Indicators: Emphasizes urgency or confidentiality: and contains suspicious attachments or links.
At this point my scenario ended as all the true positives were identified!
Description:
This alert was triggered by an inbound email contains one or more external links due to potentially suspicious characteristics. As part of the investigation, check firewall or proxy logs to determine whether any endpoints have attempted to access the URLs in the email and whether those connections were allowed or blocked.
datasource: email
timestamp: 11/20/2025 20:05:55.489
subject: Action Required: Finalize Your Onboarding Profile
sender: onboarding@hrconnex.thm
recipient: j.garcia@thetrydaily.th
attachment: None
content:
Hi Ms. Garcia,\n\nWelcome to TheTryDaily!\n\nAs part of your onboarding, please complete your final profile setup so we can configure your access.\n\nKindly click the link below:\n\n<a href=”https://hrconnex.thm/onboarding/15400654060/j.garcia”>Set Up My Profile</a>.\n\nIf you have questions, please reach out to the HR Onboarding Team.
direction: inbound
Another false positive. Similar to the first one!
Answer: No answer needed
Hurrah!
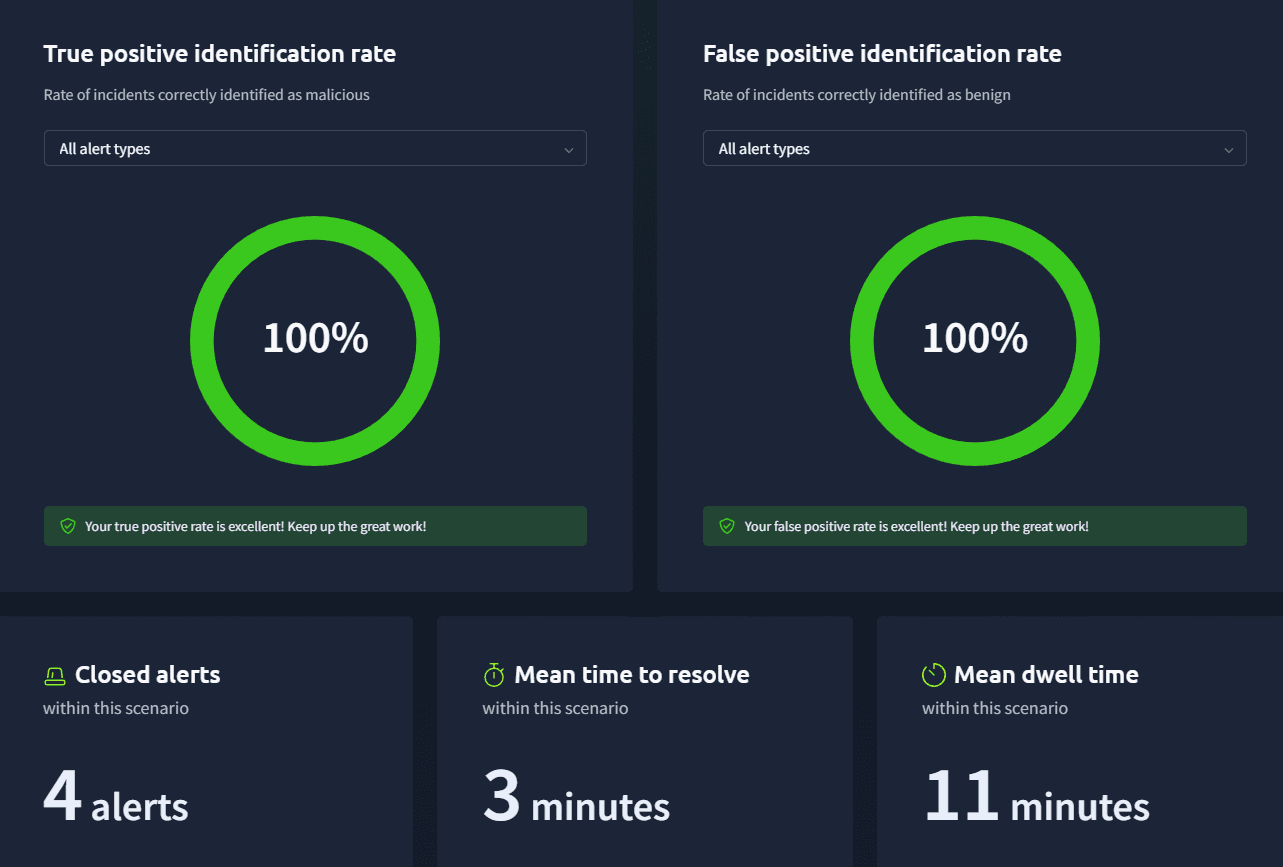
Answer: No answer needed.
Congratulations on completing this introduction to Phishing scenario on the TryHackMe SOC Simulator. At this point in our education we have of course not completely at all about SOC systems, so some of the techniques or tools required were maybe not immediately clear to you. The important thing here is to showcase how a SOC L1 analysts job actually feels like, and I hope you enjoyed this short scenario.
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other TryHackMe SOC Level 1 Path walkthrougs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] SOC Simulator: Introduction to Phishing […]