Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the Introduction to SOAR Room on TryHackMe. What is SOAR I hear you say? SOAR stands for Security Orchestration, Automation, and Response, and is all our automation of manual security processes.

Room URL:
https://tryhackme.com/room/soar
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
To defend against attacks, a SOC team relies on various security solutions, such as SIEM, EDR, firewalls, and threat intelligence platforms. They also communicate with IT and management teams as part of their processes. However, as threats grow more complex and advanced, SOC teams face challenges like alert fatigue, manual processes, too many disconnected tools, and difficulties in communication across teams.
In this room, we will explore how the Security Orchestration, Automation, and Response (SOAR) tool overcomes these challenges for a SOC team.
A look at the following rooms would be helpful before starting this room:
Answer: No answer needed
A Security Operations Center (SOC) is a centralized hub for monitoring and protecting an organization’s digital assets. Its purpose is to improve incident handling through continuous monitoring, analysis, and response. SOCs combine people, processes, and technology to achieve this.
We call the experience of an overload of events, which overwhelm analysts, alert fatigue.
Answer: Alert Fatigue
Security Orchestration, Automation, and Response (SOAR) is a tool that unifies all security tools in a SOC (SIEM, EDR, firewalls, IAM, ticketing systems) into a single interface. It streamlines investigations, provides case management, and reduces manual effort.
We call this process orchestration.
Answer: orchestration
Playbooks are predefined steps that tell the SOAR how to investigate an alert. Without SOAR, analysts often also use playbooks to go through a munual process.
Answer: Playbook
Playbooks are predefined workflows that guide how alerts are investigated and remediated. They automate repetitive steps but still involve SOC analysts for critical decisions.
While SOAR reduces repetitive manual process burden, SOC analysts’ roles remain essential for crucial decisions and verifications.
Answer: Yay
Look at the flow diagram of the SVE playbook in the room. On it you can see that in the first step new CVEs get fetched from advisory lists.
Answer: Advisory lists
If the assets are still found vulnerable, the analysts creates a mitigation plan to discuss how to mitigate further vulnerabilities.
Answer: mitigation plan
You are part of a SOC team that recently faced a large breach investigation that took ages due to a lack of automation. Your friend, McSkidy, recently advised adopting a SOAR and setting up automation workflows (also called playbooks) to help your security investigations. McSkidy sent you a checklist for a Threat Intelligence integration workflow, and your task is to figure out how it works. Click the View site button to launch the site in split view. To automate the process, use the different screens to activate the elements required for the SOAR workflow. Run and test the workflow until you get a smooth transition on the flowchart to complete the task.
Ok, let’s get going. We start by getting some instructions:
The objective is to simulate the actions of automating a SOC environment through toggling various settings. You will have to enable/disable in order to get the right combination of events to activate the flowchart.
And some more:
Adjust the Settings for automated and manual flows to adopt a SOAR and set up automation workflows that will help you in your security investigations.
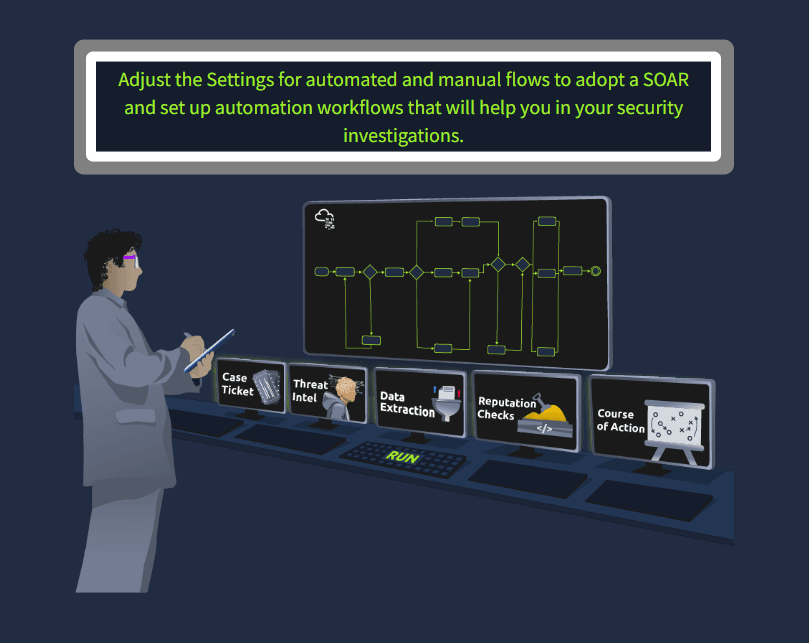
We got 5 different settings showing up: Case ticket, threat intel, data extraction, reputation checks and course of action. We need to set the correct settings for each. I will discuss them in the specified order:
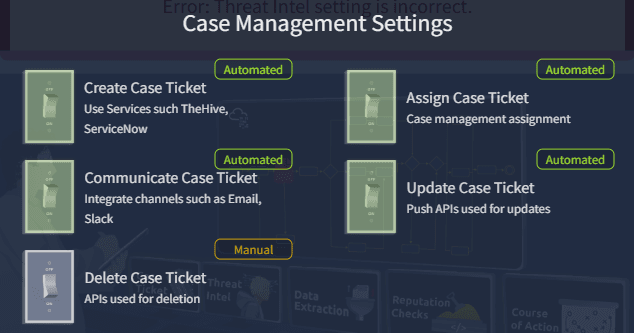
The creation, assignment, communication and updating of cases can be automated. Deletion is still better as manual process.
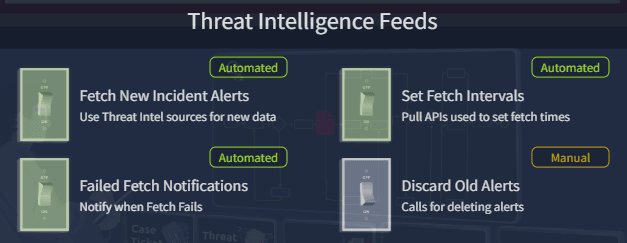
Fetching intelligence data, intervals, and failed fetches should be automated. Again, deletion of alerts is better done manually.
We can extract domains, IPs, URL automatically, but for unknown/new threats manual labor is required.

We can automatically output results from VirusTotal, but running tests and validating and confirming needs to be done manually.

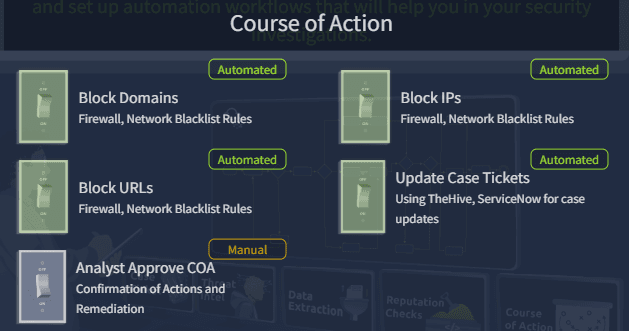
Again, we can block domains, IPs and URLs, and update case tickets, but analyst approval needs to happen manually.
Answer: THM{AUT0M@T1N6_S3CUR1T¥}
That’s all for this room. In this room, we looked at the traditional SOC processes and their challenges. Then we saw how SOAR can overcome these challenges through its Orchestration, Automation, and Response. Finally, we examined some real playbooks used in a SOC and developed a Threat Intelligence workflow for automation.
Answer: No answer needed.

Congratulations on completing Introduction to SOAR. I found this to be a really great practice room for getting some experience with Wireshark. I don’t know about you, but I learned a lot!
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other TryHackMe SOC Level 1 Path walkthroughs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] Introduction to SOAR […]