Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the Humans as Attack Vectors room on TryHackMe. In this room we discuss how humans can be targeted in different ways by cyber threats, and how SOC professionals help defend them.

Room URL:
https://tryhackme.com/room/humansattackvectors
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
The Security Operations Center (SOC) might sound technical and impressive, but what does it really protect us from? In this room, you will dive into the methods of modern attackers and explore how they target the weakest cyber security element – humans.
Answer: No answer needed
Attackers go after people because they can provide direct access to:
Some attackers target specific accounts, while others breach many accounts and decide later how to exploit them.
Easy enough. Humans!
Answer: Humans
Attackers are looking for access when targeting humans. Finding a backdoor into a fortness is often a lot easier than trying to scale the walls!
Answer: Access
Social engineering attacks exploit trust and emotion to bypass technical defenses. They come in many forms—emails, downloads, calls, or even physical tricks—and remain a constant risk. As a SOC analyst, recognizing these tactics is critical to defending against them.
Attacks that aim to manipulate human emotions and psychology are called social engineering attacks.
Answer: Social Engineering
The definition for this kind of social engineering method is called impersonation.
Answer: Impersonation
Even strong mitigation can be bypassed, so detection skills are critical.
Mitigation reduces risks, detection catches what slips through. SOC analysts must master both—investigating advanced attacks while also promoting measures that protect employees and lighten the SOC workload.
We talk about mitigation when we try to reduce the chance, or the effects, of an attack happening. Think climate change mitigation, but cybersec style 🙂
Answer: mitigation
If we want our employees to learn how to avoid phishing attacks, we need to educate them. In other words: security awareness training. Unforuntately we can’t expect everyone to spend learning about cybersecurity on TryHackMe 😀
Answer: Security awareness training
Every organization faces constant attacks targeting its employees. However, the role of the SOC in responding to these attacks can vary. In some teams, analysts just monitor alerts. In others, they are deeply involved in the company’s processes. Analysts may:
View Site
For this lab, imagine yourself as a SOC analyst at TryHackMe. Open the security dashboard by clicking the View Site button, protect your coworkers at Employees at Risk, and make TryHackMe more secure at Security Policy tab. Once completed, claim the flags and answer the task questions!
Open the site. You will see a security dashboard:
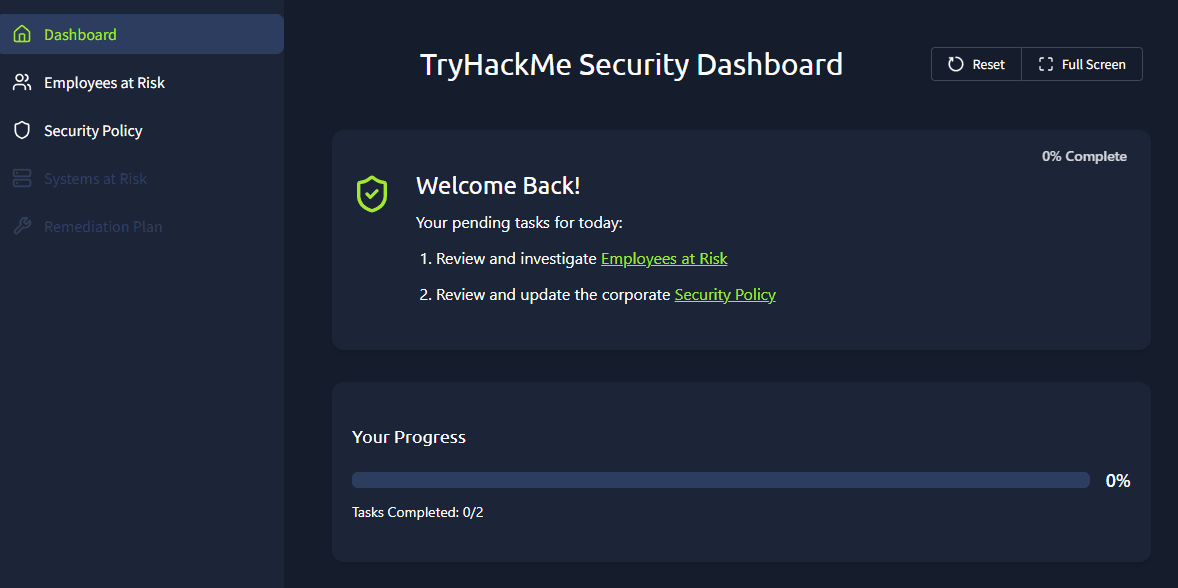
To get started press Employees at Risk in the menu, or the link in the welcome back message. You will be met by four cases. Let’s cover them here.
Hey, I am a new software engineer. I urgently need 7-Zip archive software, but it doesn’t launch. Can you review if it’s because of your security tools?
Upon investigation, you see a “Setup.exe” downloaded from best-freeapps-2025.top, a new freeware hosting site. Lucas tried to launch it 6 times but was blocked by an antivirus. How would you respond to Lucas?
Your Verdict
Quarantine the Setup.exe. Instruct Lucas to use the official 7-Zip installer. A freeware hosting site seems way to suspicous. 7-Zip can be easily installed through their official site, and maybe the company has a software installation portal?
Title: Stripe Invoice #38291 – Payment Succeeded
From: noreply@stripe-payments.xyz
To: Mark Phillips, Finance Director
Content: This email confirms the $23,650.00 payment from TryHackMe according to invoice #38291. For details, kindly see the attached Invoice.rar (password: 1111). If you have any questions, please get in touch with us at support@stripe.com.
Your Verdict
Block the email and start the analysis. This is an email phishing attempt. This is clearly a social engineering/phishing attempt. The mail is created to scare the reader. But they payment is unrealistically high anway, and attached archives is even more of a red flag. stripe-payments.xyz is a fake domain as well!
Hi, I just got a phone call from our CEO, Ben. He asked me to reset his Gmail password since he has some issues with login. Of course, I approved it. But why did he call at 9 PM and from a hidden number? Doesn’t it look suspicious?
You check the logs and see a login from the USA, the same country Ben lives in. Ben does not respond to your messages or phone calls. What would you do?
Your Verdict
Disable Ben’s Gmail account until he confirms the login or is back in the office. I would definately disable the account, since we could not confirm the case with Ben. Him calling from hidden number is quite suspicious, and we can’t take any chances since he is the CEO. He will understand having to wait till tomorrow if it really is him, which I doubt. It is likely a deepfake.
User: Rose Lewis, HR Assistant
Login To: Microsoft 365
Login Location: London, UK
Typical Location: Oxford, UK
Visited URLs Before Login:
– http://login[.]micrsoft365-online[.]ru
– https://hroyhiqtspqgkp[.]info
– https://mail[.]tryhackme[.]thm
Your Verdict
Disable the account of Rose Lewis until you are more confident in your verdict. The http://login[.]micrsoft365-online[.]ru link seems like a false login page. It is likely that Rose tried logging in on a Russian Microsoft looking page, and lost access to her account after.
We got the flag!
Answer: THM{anyone_else_at_risk?}
Next up, security policy challenge!
We need to select 4 policies out the following policies to make THM more secure:
Strict Access Management
Require SOC analysts to approve every login to the corporate email manually
NO! This would be impossible to manage.
Security Awareness Program
Setup quarterly trainings for all employees on how to detect and report modern phishing techniques
YES! Wonderful idea and will help a lot.
Internet Restrictions
Limit Internet access for all employees to only corporate resources
NO! While this would remove a lot of risks, we can’t just limit the internet. This is not North Korea you know.
Access Management Policy
Document how your IT support should verify requests like password reset or access approval
YES! This is great to have documentation and policy on.
Vulnerability Scanning
Conduct weekly vulnerability scans of all corporate servers and laptops
Quite a great idea, but it won’t help us against social engineering and phishing attacks.
Antivirus Solution
Purchase and install a reliable antivirus on all workstations of the employees
YES! Even though other protection layers (EDR, IPS, physical firewalls etc) should do the job, having a antivirus solution on all workstations will protect us even better.
Anti-Phishing Solution
Purchase and deploy a solution to detect and automatically block most phishing emails
YES! There are great solutions out there that can stop phishing attacks before they reach people.
Anway this is how your policies should look like:
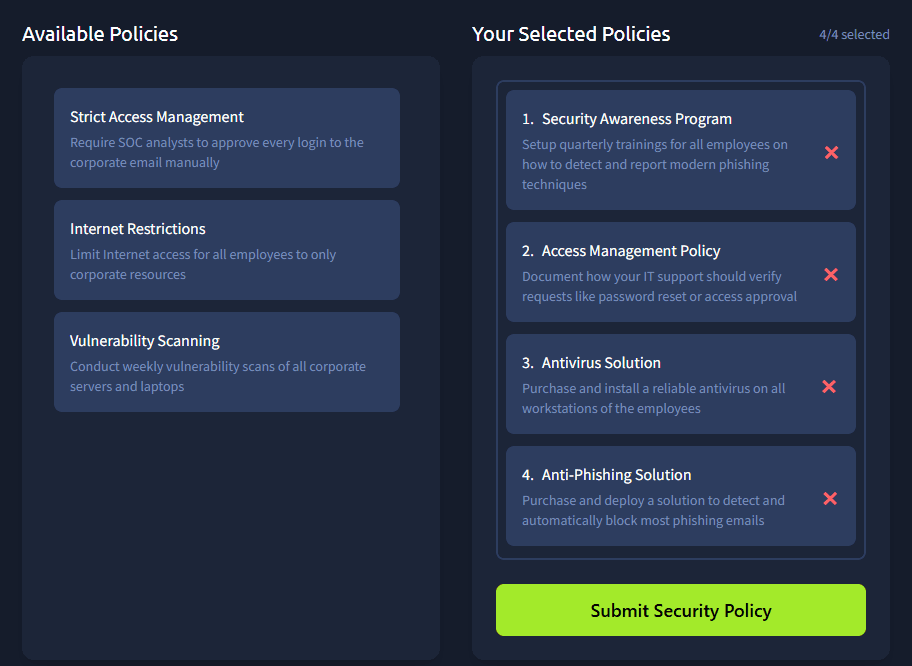
And submitting these gives us the flag.
Answer: THM{human_protection_expert!}
In this room, you explored attacks on humans, the weakest element in cyber security. You have discovered how and why attackers target people and how you, as a SOC analyst, can detect and prevent it. But your journey shouldn’t stop here. As threats evolve, staying informed about the latest attack trends is key to your success in the SOC. Here are a few great sites to follow:
Answer: No answer needed.
Congratulations on completing Humans as Attack Vectors. This room puts a lot of great focus on the human element of cyber security. I hope you understand that you can be a cyber security ninja and have complete focus on the technical side of things, but it only takes one employee to completely render your defenses useless.
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other TryHackMe SOC Level 1 Path walkthroughs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] Humans as Attack Vectors […]