Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the Sakura Room on TryHackMe. I thought it was fun to try a OSINT room for a change, so let’s learn to use a variety of OSINT techniques to solve this room created by the OSINT Dojo.
Room URL:
https://tryhackme.com/room/sakura
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
This room is designed to test a wide variety of different OSINT techniques. With a bit of research, most beginner OSINT practitioners should be able to complete these challenges. This room will take you through a sample OSINT investigation in which you will be asked to identify a number of identifiers and other pieces of information in order to help catch a cybercriminal. Each section will include some pretext to help guide you in the right direction, as well as one or more questions that need to be answered in order to continue on with the investigation. Although all of the flags are staged, this room was created using working knowledge from having led and assisted in OSINT investigations both in the public and private sector.
NOTE: All answers can be obtained via passive OSINT techniques, DO NOT attempt any active techniques such as reaching out to account owners, password resets, etc to solve these challenges.
If you have any other questions, comments, or suggestions, please reach out to us at @OSINTDojo on Twitter.
Answer: Let’s Go!
The OSINT Dojo recently found themselves the victim of a cyber attack. It seems that there is no major damage, and there does not appear to be any other significant indicators of compromise on any of our systems. However during forensic analysis our admins found an image left behind by the cybercriminals. Perhaps it contains some clues that could allow us to determine who the attackers were?
We’ve copied the image left by the attacker, you can view it in your browser here.
Start by saving the image on your VM. There are many options here, but I recommend to run the following command using exiftool:
exiftool ./sakurapwnedletter.svg
This shows the following output:
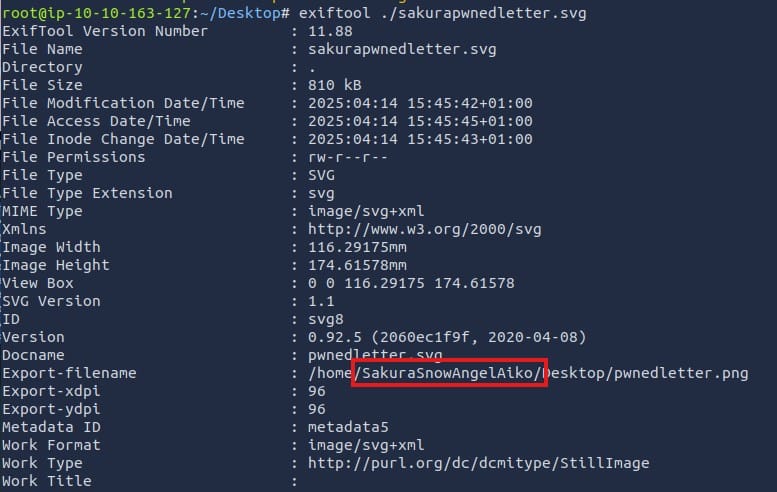
If you look carefully, you will see the home directory of the user which created the file if you look at the Export-filename field. This must be the username!
Alternatively, you can use a website such as https://processing.compress-or-die.com/ and upload the file here.
Answer: SakuraSnowAngelAiko
It appears that our attacker made a fatal mistake in their operational security. They seem to have reused their username across other social media platforms as well. This should make it far easier for us to gather additional information on them by locating their other social media accounts.
Most digital platforms have some sort of username field. Many people become attached to their usernames, and may therefore use it across a number of platforms, making it easy to find other accounts owned by the same person when the username is unique enough. This can be especially helpful on platforms such as on job hunting sites where a user is more likely to provide real information about themselves, such as their full name or location information.
A quick search on a reputable search engine can help find matching usernames on other platforms, and there are also a large number of specialty tools that exist for that very same purpose. Keep in mind, that sometimes a platform will not show up in either the search engine results or in the specialized username searches due to false negatives. In some cases you need to manually check the site yourself to be 100% positive if the account exists or not. In order to answer the following questions, use the attacker’s username found in Task 2 to expand the OSINT investigation onto other platforms in order to gather additional identifying information on the attacker. Be wary of any false positives!
Time for some search machines work. Let’s search for SakuraSnowAngelAiko.
I immediately found a Github page:
https://github.com/sakurasnowangelaiko
As well as a X profile:
https://x.com/sakuraloveraiko?lang=en
We can see a bunch of interesting Tweets, both of WIFI information and some photos. We can have a look at these later, since now we are only interested in the email address.
I tried looking around on the Github account, and tried finding the associated email. They were not visible unfortunately. I also tried to look in the commit history, since sometimes you can see the email address when looking at individual commit and adding .patch at the end of the URL. Source
When looking at this commit though:
https://github.com/sakurasnowangelaiko/IO/commit/d4778c338b0cbe98da7da6c6fad6d03aad6cff54.patch
Unfortunately, the email is hidden.
I found two interesting repositories. One of them is some kind of mining script:
https://github.com/sakurasnowangelaiko/ETH
We will have a look at that one later.
Another interesting repository I found was the following:
https://github.com/sakurasnowangelaiko/PGP
PGP stands for Pretty Good Privacy (PGP) and is an encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for signing, encrypting, and decrypting texts, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications
According to research, the public PGP key includes metadata, including the email address associated with the key! We can decode this information from they key on a page like:
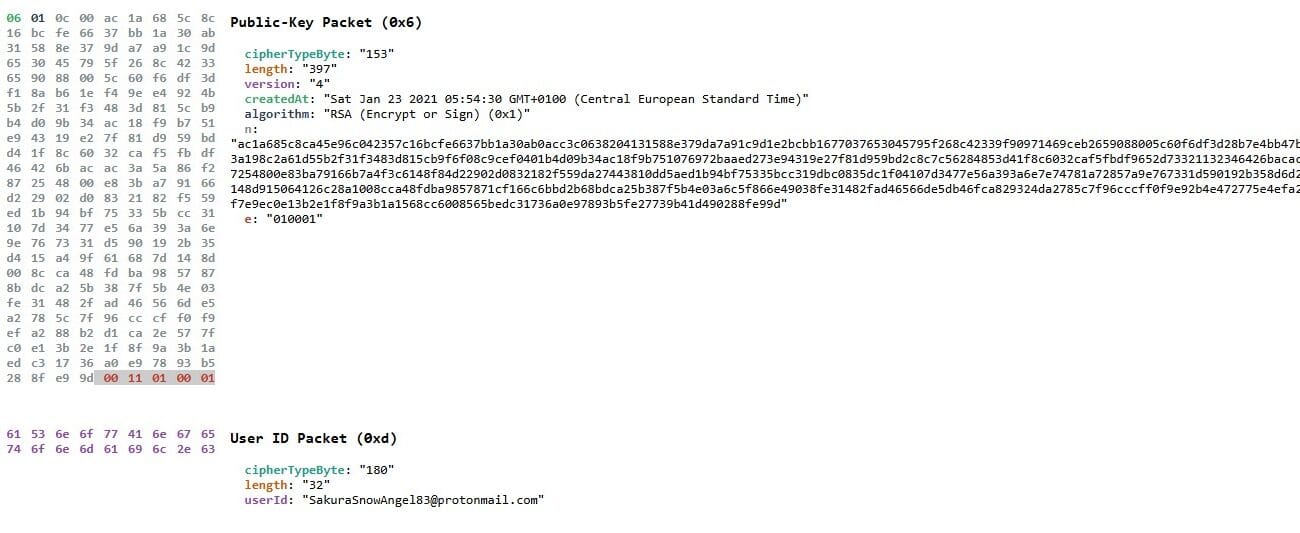
What we see here in the bottom is the email address!
Answer: SakuraSnowAngel83@protonmail.com
This one is easier. While looking at the Tweets earlier I came across the following one:
It sure sounds like his real name i Aiko Abe!
Answer: Aiko Abe
It seems the cybercriminal is aware that we are on to them. As we were investigating into their Github account we observed indicators that the account owner had already begun editing and deleting information in order to throw us off their trail. It is likely that they were removing this information because it contained some sort of data that would add to our investigation. Perhaps there is a way to retrieve the original information that they provided?
On some platforms, the edited or removed content may be unrecoverable unless the page was cached or archived on another platform. However, other platforms may possess built-in functionality to view the history of edits, deletions, or insertions. When available this audit history allows investigators to locate information that was once included, possibly by mistake or oversight, and then removed by the user. Such content is often quite valuable in the course of an investigation. In order to answer the below questions, you will need to perform a deeper dive into the attacker’s Github account for any additional information that may have been altered or removed. You will then utilize this information to trace some of the attacker’s cryptocurrency transactions.
The room mentions that we should look at the history of content. Since I earlier found the miningscript repository, let’s have a look at that one:
https://github.com/sakurasnowangelaiko/ETH
If you look at the miningscript contents there are no real credentials in there:
https://github.com/sakurasnowangelaiko/ETH/blob/main/miningscript
But what about the commit history? You can find the commit history here:
https://github.com/sakurasnowangelaiko/ETH/commits/main/
Open up the bottom one. This is the one where the file got created:
https://github.com/sakurasnowangelaiko/ETH/commit/5d83f7bb37c2048bb5b9eb29bb95ec1603c40135
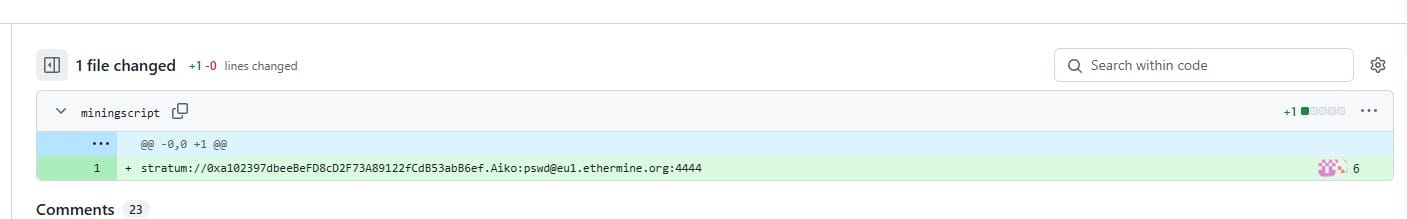
Interesting! There are some credentials in there and more!
stratum://0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef.Aiko:pswd@eu1.ethermine.org:4444
Let’s break it down:
0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef: Ethereum wallet address format (starts with 0x and is 42 characters long).
ethermine.org: Ethermine is a well-known Ethereum mining pool.
stratum://: This is the protocol used for mining pool communication.
:4444: The port used by Ethermine’s Ethereum mining pool.
We got our answer. The cryptocurrency is Etherium!
Answer: Ethereum
We found this earlier as part of the connection string.
Answer: 0xa102397dbeeBeFD8cD2F73A89122fCdB53abB6ef
I tried searching for the wallet address in Google and came across the following pages which shows all payments to and from this wallet:
https://etherscan.io/address/0xa102397dbeebefd8cd2f73a89122fcdb53abb6ef
One of the payments is on the correct date:
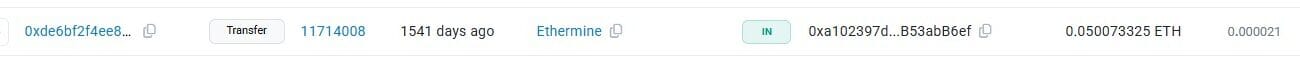
| 0xde6bf2f4ee82f9176a2c491aef75737e4a2c7be38e48bdedbc10aba5dbb996fd | Transfer | 11714008 | 1541 days ago | Ethermine | IN | 0xa102397d…B53abB6ef | 0.050073325 ETH | 0.000021 |
Here we can see that it originates from the Ethermine mining pool.
Answer: Ethermine
Have a look around at all the transactions. You should see 3 transactions which are made in the Tether cryptocurrency:
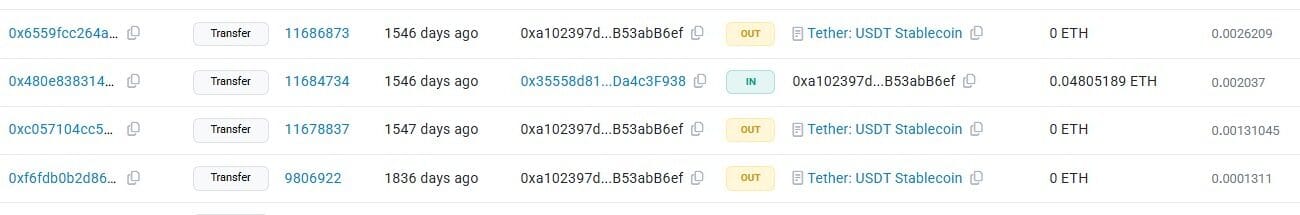
Answer: Tether
Just as we thought, the cybercriminal is fully aware that we are gathering information about them after their attack. They were even so brazen as to message the OSINT Dojo on Twitter and taunt us for our efforts. The Twitter account which they used appears to use a different username than what we were previously tracking, maybe there is some additional information we can locate to get an idea of where they are heading to next?
We’ve taken a screenshot of the message sent to us by the attacker, you can view it in your browser here.
Although many users share their username across different platforms, it isn’t uncommon for users to also have alternative accounts that they keep entirely separate, such as for investigations, trolling, or just as a way to separate their personal and public lives. These alternative accounts might contain information not seen in their other accounts, and should also be investigated thoroughly. In order to answer the following questions, you will need to view the screenshot of the message sent by the attacker to the OSINT Dojo on Twitter and use it to locate additional information on the attacker’s Twitter account. You will then need to follow the leads from the Twitter account to the Dark Web and other platforms in order to discover additional information.
Have a look at the image:
https://raw.githubusercontent.com/OsintDojo/public/main/taunt.png
You might recognize the picture from the earlier Twitter/X account we found. I suppose this is the current one, while the other one we found after was his old account (or secondary?). Anyway, the current X account is @SakuraLoverAiko found here:
Answer: SakuraLoverAiko
Look at the fourth post on X. Here Aiko posts the following hexadecimal:
b2b37b3c106eb3f86e2340a3050968e2On the post before that he also mentions that:
Anyone who wants them will have to do a real DEEP search to find where I PASTEd them.
If you are like me, and don’t want to visit the DarkWeb, luckily someone on Reddit did it for us:
https://raw.githubusercontent.com/OsintDojo/public/main/deeppaste.png
Here you see the SSID of his home network:
DK1F-G
Now, there exists are service called wigle at https://wigle.net/. Here you can sign up and search with the SSID and voila, you will receive the BSSID (here called Net ID).
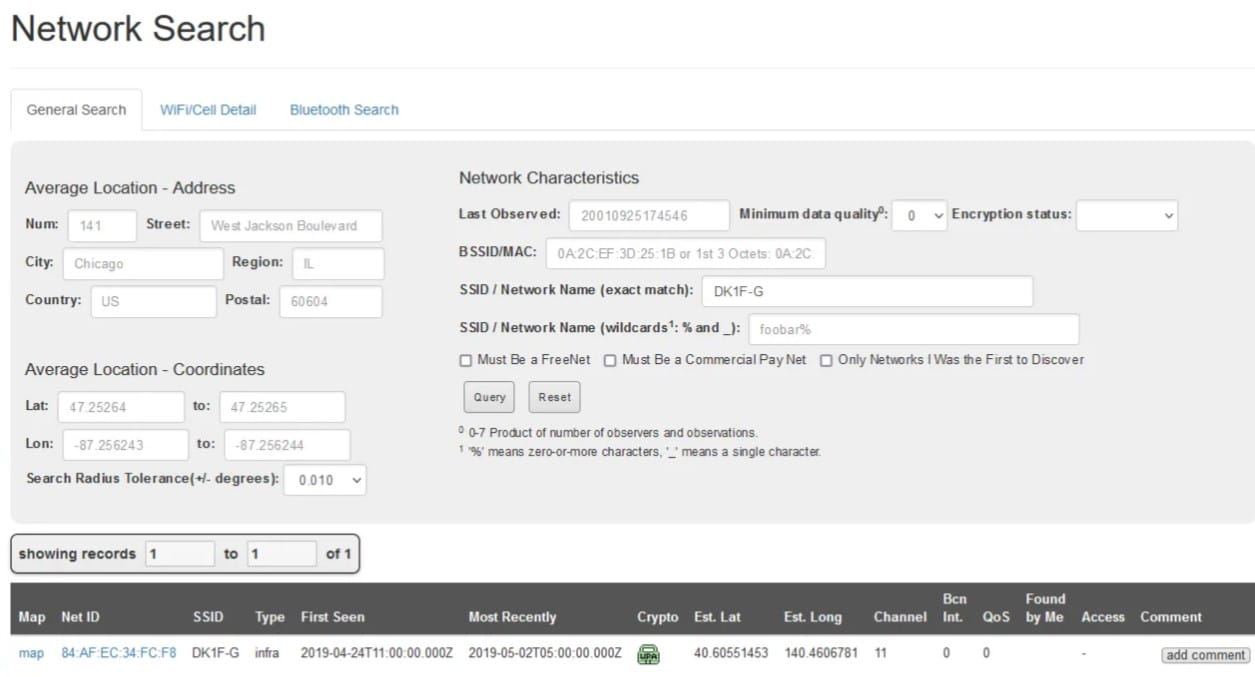
Answer: 84:AF:EC:34:FC:F8
Based on their tweets, it appears our cybercriminal is indeed heading home as they claimed. Their Twitter account seems to have plenty of photos which should allow us to piece together their route back home. If we follow the trail of breadcrumbs they left behind, we should be able to track their movements from one location to the next back all the way to their final destination. Once we can identify their final stops, we can identify which law enforcement organization we should forward our findings to.
Instructions
In OSINT, there is oftentimes no “smoking gun” that points to a clear and definitive answer. Instead, an OSINT analyst must learn to synthesize multiple pieces of intelligence in order to make a conclusion of what is likely, unlikely, or possible. By leveraging all available data, an analyst can make more informed decisions and perhaps even minimize the size of data gaps. In order to answer the following questions, use the information collected from the attacker’s Twitter account, as well as information obtained from previous parts of the investigation to track the attacker back to the place they call home.
The question is referring to the photo shared in this Tweet:
Notice the tall statue on the background? I use google reverse search on that part of the image and quickly got led to the following page:
https://www.wikidata.org/wiki/Q178114
This seems to be the Washington monument!
A quick look at Google Maps shows that there are only 2 airports in Washington, of which the Ronald Reagan Airpot is closest:
The abbreviation for this airport is DCA.
Answer: DCA
Now we are being referred to this Tweet:
We can clearly see two important elements on the picture. First there is a JAL – First Class Lounge Sakura Lounge located at the airport. In addition there is a sign with the text: 5 star airline SKYTRAX, and then I think it says Japan Airlines in the bottom. I also checked the metadata, but there was no location data attached to the photo.
So it is definitely an airport Japan Airlines flies from hmm. Now we just need to find out where they have these Sakura lounges. Some quick searching led me to the following page with all their Sakura Lounges:
https://www.jal.co.jp/jp/en/inter/service/lounge
Maybe we can identify the design on the lounge pictures? On some more thinking I noticed that First Class Lounges and Sakura Lounges are 2 different categories. So this lounge has both classes, which means it might make the pool slightly smaller. Based on the map shared on the Twitter page we now he is probably flying back to Japan. This reduces the selection to two airports.
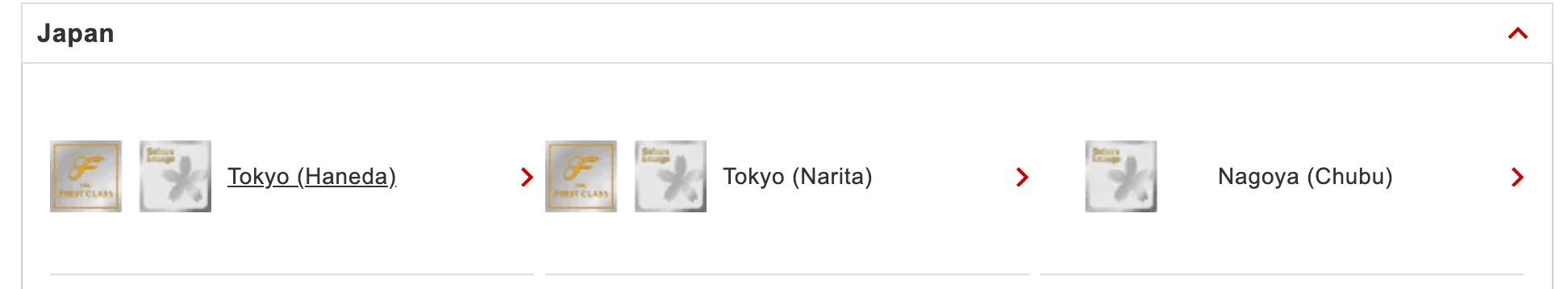
I had trouble manually identifying the correct airport, and realised that I forgot to reverse image search the image:
https://tineye.com/search/4af721d306d4b3f20cc0e9a3db3539164c02a969?sort=score&order=desc&page=1
Here I found this page:
https://4travel.jp/travelogue/11143943?lid=prev_travelogue_from_travelogue
This person covers his journey flying from Tokyo Haneda airport, and includes the entrance in the photo. Furthermore, we can confirm this as Tokyo Haneda Airport is a 5 star Skytrax lounge: https://skytraxratings.com/airline-lounges/japan-airlines-lounges-at-tokyo-haneda-airport
Finally, I came across another review from the Tokyo Haneda airport, and here we see a picture from the same location (Photo 2):
https://cultureguru.nl/index.php/2017/08/02/japan-airlines-sakura-lounge-at-haneda-airport-international-terminal/
So yes, this is Tokyo Haneda airport, HND.
Answer: HND
The question refers to this picture:
https://x.com/SakuraLoverAiko/status/1353733617487241217/photo/1
Knowing the general shape of Japan, the area on the map looks like from the direction North of Tokyo. I quickly noticed the island on the left, which way easy to find on Google Maps:
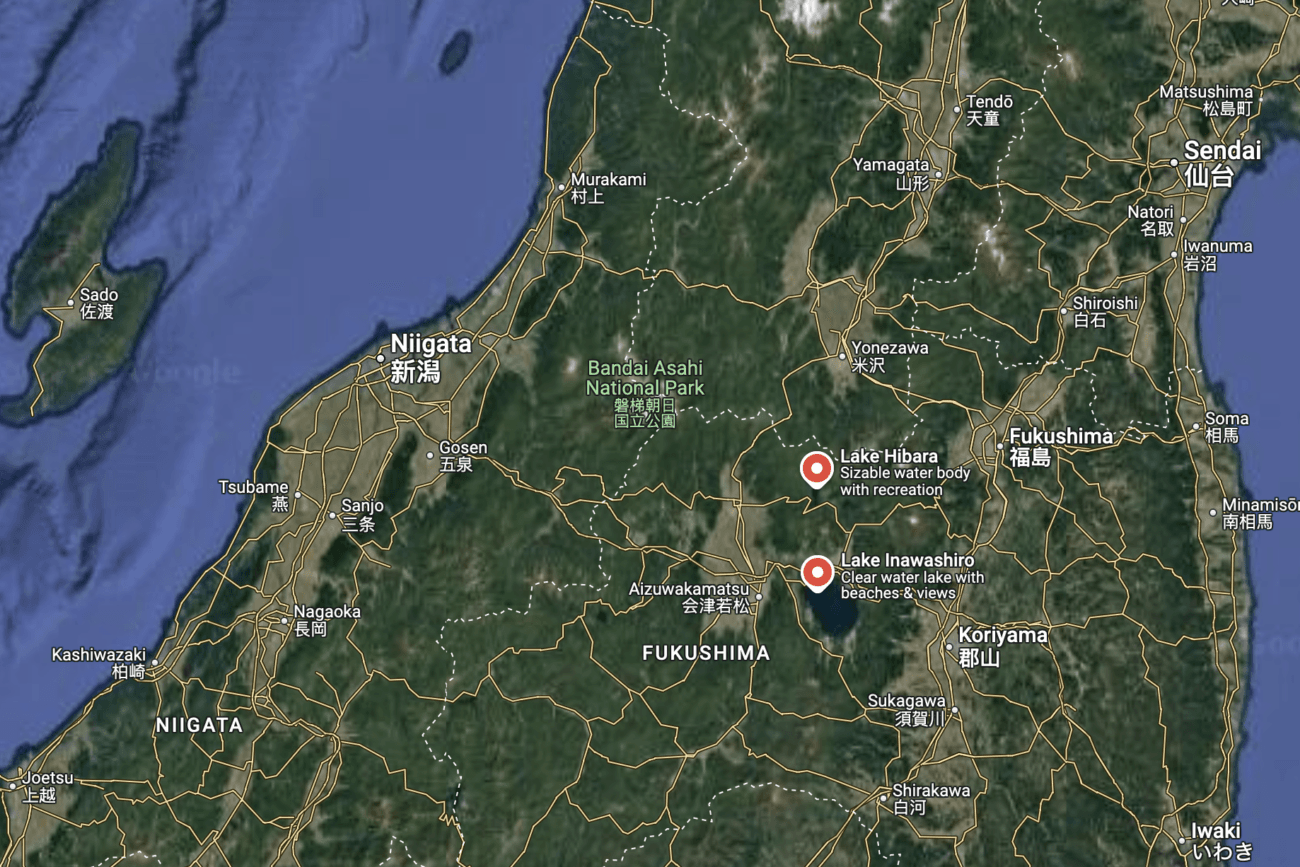
It is called Sado Island. I finally search for lakes, and found that the large lake is called Lake Inawashiro.
Answer: Lake Inawashiro
Let’s think back on the whole investigation. We know Aiko loves cherry trees, and we also know that he lives somewhere north of Tokyo. But we have some geographic data! We did find the BSSID of his home network, and wigle gave us the coordinates!
lat: 40.60551453
lon: 140.460681
Checking this lat and lon on the web shows us a location in the city of Hirosaki:
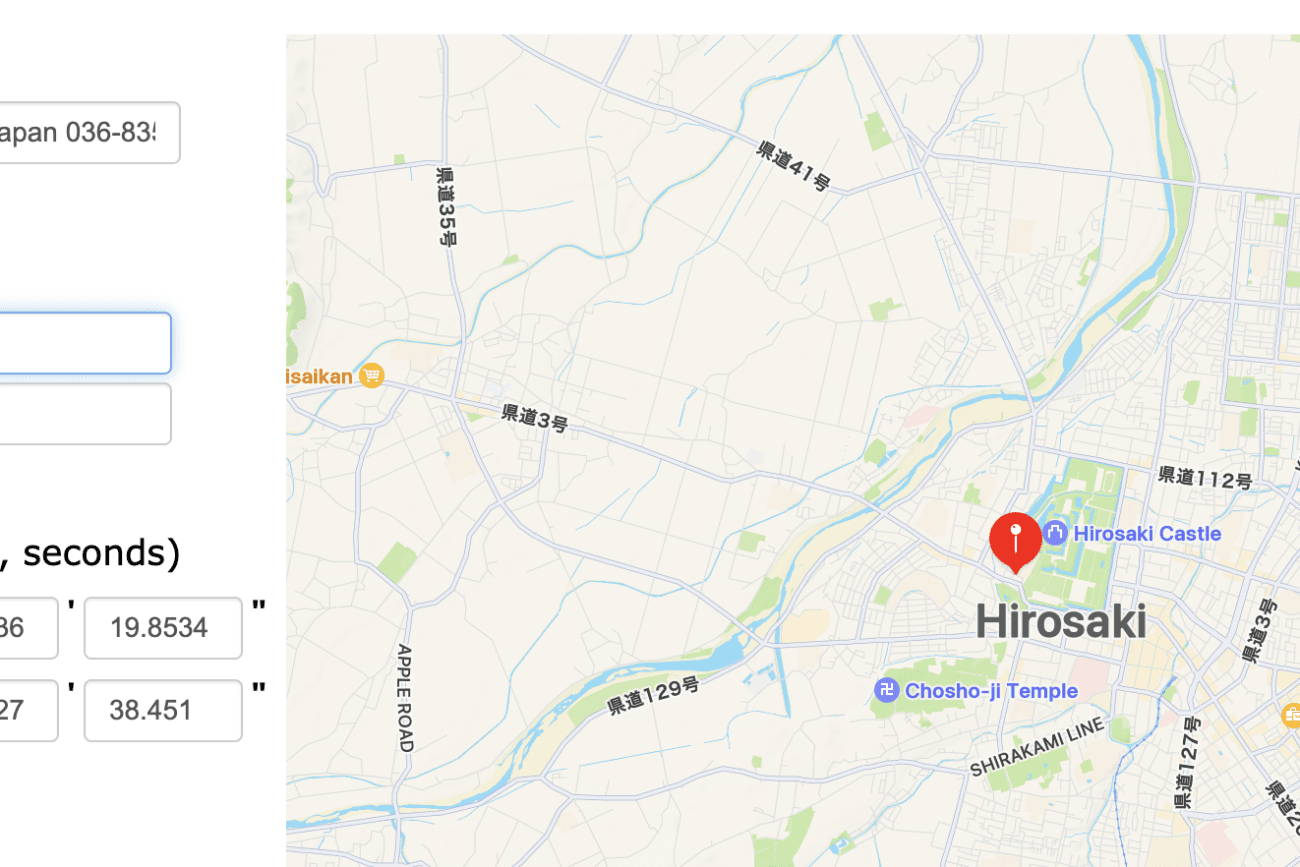
A quick look at Wikipedia shows us that Hirosaki is far north of Tokyo:
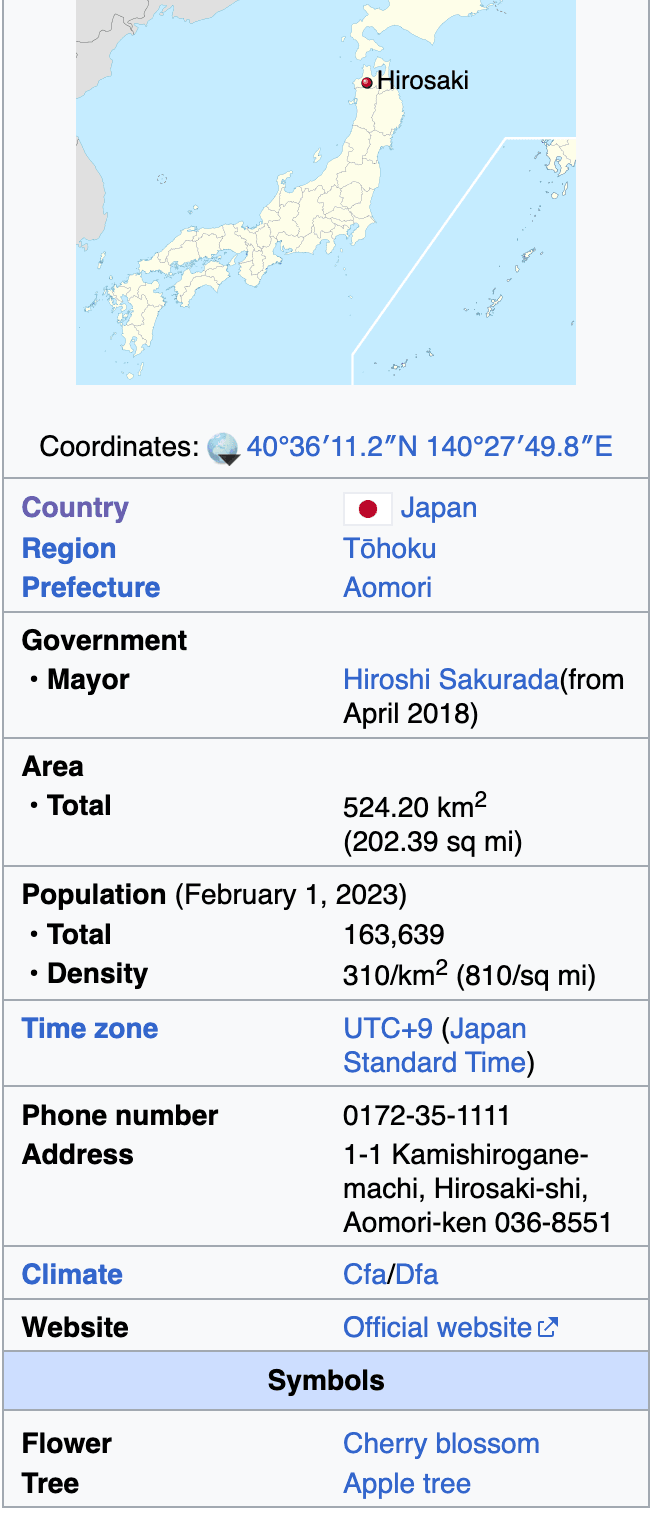
And another fun fact, the symbol flower of the city is Cherry! Coincidence, maybe, but Hirosaki is the answer 🙂
Answer: Hirosaki

Congratulations on completing the Sakura Room!. I REALLY like this room, and love the fact that we got to stitch together a great amount of data to finally form some pure intelligence in the end. OSINT is great fun, and I will definitely cover more of it in the future!
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link: