Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Hi! In this walkthrough we will be looking at the TryHackMe: Nmap room. Nmap is an fundamental skill required for basicly all penetrating testing projects and CTFs, and allows us to gain a massive amount of information on any network we are investigating.
Let’s cover all the theory and questions together!

Room URL: https://tryhackme.com/room/furthernmap
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by THMs rooms. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Nothing to do here besides deploying the target machine.
Answer: No answer needed.
Let us assume that you have the IP address of your target machine. The first steps of gathering data on the machine is to find out what services are running on the machine. We do this by scanning its ports. A machine needs to have certain ports open to run certain services, and by scanning its ports we can figure out which services it runs by looking at which ports are open.
Network connections are made between two ports — an open port listening on the server and a randomly selected port on your own computer. For example, when you connect to a web page, your computer may open port 49534 to connect to the server’s port 443. Every computer has 65535 available ports, of which many are registered as standard ports. HTTP for example, runs on port 80, while HTTPS runs on port 443. It is however not guaranteed that services run on their default port, which makes port scanning even more important!
Nmap is a tool that provides us with the power to do quick and efficient port scanning.
What networking constructs are used to direct traffic to the right application on a server?
Port numbers help identify specific services or applications running on a device. For example, HTTP traffic typically uses port 80, and HTTPS uses port 443. The answer is ports.
Answer: Ports
Every computer has 65535 available ports.
Answer: 65535
In networking, well-known ports are port numbers ranging from 0 to 1023. These ports are reserved for widely used services and protocols, ensuring that applications can reliably communicate over the network.
The Internet Assigned Numbers Authority (IANA) maintains a registry of these well-known ports, assigning specific numbers to various services. For example, port 80 is assigned to HTTP, port 443 to HTTPS, and port 25 to SMTP.
Answer: 1024
Nmap can be accessed by typing nmap into the terminal command line, followed by some of the “switches” (command arguments which tell a program to do different things) we will be covering below. You can get an overview of all switches by writing:
nmap -hor
man nmapEnter your help command of choice (I tend to use man nmap).
If you scroll down a bit you will come across the port scanning techniques section. The first switch listed here is the -sS TCP SYN scan.

Answer: -sS
Scroll down a little bit from the previous question. You will come across the section covering UDP scans.
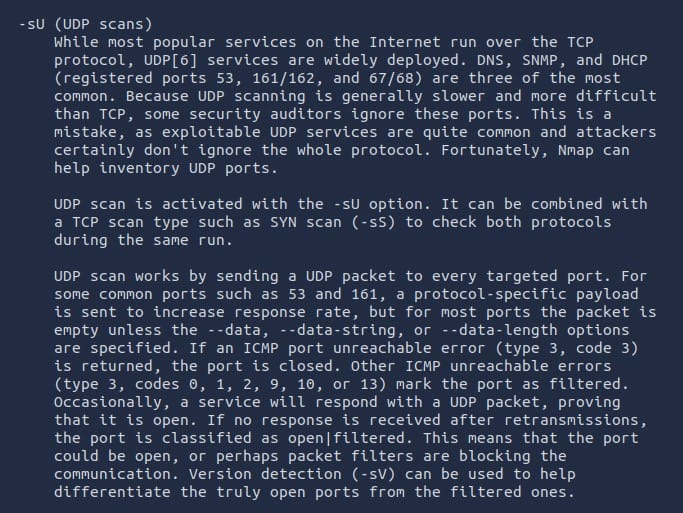
Answer: -sU
Most often you can get what you need by looking at the summary section at the top.

If you look in the bottom you can see the correct flag is -O.
Answer: -O
Also on the above screenshot. The service/version detection flag is -sV.
Answer: — sV
You get the drill now I suppose. But if you are feeling lazy here is the second part of the options summary section.

The flag to increase verbosity is -v.
Answer: -v
This can be read just after the answer of the previous section. You just add another v! (you can even add more!)
Answer: -vv
We should always save the output of our scans — this means that we only need to run the scan once (reducing network traffic and thus chance of detection), and gives us a reference to use when writing reports for clients.
See the previous screenshot: -oA <basename>: Output in the three major formats at once.
Answer: -oA
Again: -oN <file>: Output scan in normal
Answer: -oN
oG <file>: Output scan in Grepable format
Answer: -oG
Look at the MISC section on the previous screenshot.
We can use the -A flag: Enable OS detection, version detection, script scanning, and traceroute.
Answer: -A
This is found in the TIMING AND PERFORMANCE section. -T<0-5>: Set timing template (higher is faster)
Answer: -T5
-p <port ranges>: Only scan specified ports
You can both enter single port numbers seperated by a comma, or enter a range.
Ex: -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9
Answer: -p 80
You can enter a range by using a ‘-‘ between the numbers.
Answer: -p 1000–1500
We can scan all ports by using -p-. This is not recommended as it will take a bunch of time! It is better to focus on the most common ports first, and let a complete scan running in the background afterwards while you do web enumeration.
Answer: -p-
Use the -script flag.
–script=<Lua scripts>: <Lua scripts> is a comma separated list of directories, script-files or script-categories
Answer: –script
All scripts in the vuln category can be run by entering –script=vuln. There exists a lot of other categories, which we will cover later.
Answer: – script=vuln
When port scanning with Nmap, there are three basic scan types. These are:
Additionally there are several less common port scan types:
Answer: No answer needed.
To understand TCP Connect Scans, it is important to have knowledge about the three-way handshake. To remind you, the three-way handshake consists of three parts:
Nmaps TCP Connect scan uses this three-way handshake method with each target port in turn. It checks the response it receive for each port to determine whether the port is open or closed.
For example: if Nmap sends a TCP request with the SYN flag set to a closed port, the target server will respond with a TCP packet with the RST (Reset) flag set. Nmap can therefore conclude that the port is closed.
If on the other hand the target port is open, the target will respond with a TCP packet with the SYN/ACK flags set. Nmap then marks this port as being open and completes the handshake by sending back a TCP packet with ACK set.
There is a third possibility though: the port is open but hidden behind a firewall. Many firewalls simply drop incoming packets. This means that Nmap will receive nothing after sending a TCP SYN request. The port is considered to be filtered. Firewalls can however be setup to respond with a RST TCP packet instead, which makes it difficult to gain knowledge about the port.
RFC refers to the the RFC Series (ISSN 2070-1721) contains technical and organizational documents about the Internet, including the specifications and policy documents produced by five streams. Some quick googling shows us that the TCP protocol is defined in RFC 793:
https://www.rfc-editor.org/rfc/rfc793
Answer: RFC 793
If a port is closed the target server wil respond with the rest flag (RST).
Answer: RST
Syn scans are very similar to TCP Connect scans. SYN scans are often referred to as ‘half-open’, or ‘stealth’ scans. The difference is that SYN scans do not perform a full three-way handshake in the sense that they send back a RST TCP package in the third step, instead of a ACK. This prevents that the server will repeatedly try to make the request.
This can have different advantages:
There are also two disadvantages:
Because of these strong advantages SYN scans are the default scan type.
The SYN scan is also called Half-Open or Stealth. The reason for this name is that the scan is considered more stealthy than the TCP Connect scan as it does not create a complete connection with the target server, and therefore is less visible.
Answer: Half-Open, Stealth
No. One of the disadvantages of the SYN scan is that they need sudo permissions.
Answer: N
While TCP connections have a state initiated with a three-way handshake, UDP are stateless. This means that UDP connection send packets to the target port with a hope that they arrive, but no guarantee. Due to being stateless, UDP connections are very quick, but make them difficult and slower to quick.
The switch for an Nmap UDP scan is -sU.
Since UDP scans are so slow it’s usually good practice to run an Nmap scan with –top-ports <number> enabled. For example, scanning with nmap -sU --top-ports 20 <target>. Now only the 20 most common ports get scanned.
When sending a UDP packet to an open UDP port there should be no response. Nmap can in this case only conclude that the port is either open or filtered. It suspect that the port is open, but it could still be firewalled. If it does receive a response the port is marked as open, but this does not happen often. When a packet is sent to a closed UDP port, the target should respond with an ICMP (ping) packet containing a message that the port is unreachable.
If the port does not respond to a UDP scan, it is either open or filtered (protected by a firewall). Since both these cases do not respond to the scan, nmap can’t conclude more.
Answer: open|filtered
When a packet is sent to a closed UDP port, the target should respond with an ICMP (ping) packet containing a message that the port is unreachable.
Answer: ICMP
NULL, FIN and Xmas TCP port scans are not used as commonly as the previously discussed port scan types. What these three scan types have in common are that they are even stealthier than a SYN scan.
The expected response for open ports with these scans is also identical, and is very similar to that of a UDP scan. If the port is open then there is no response to the malformed packet. Unfortunately (as with open UDP ports), that is also an expected behavior if the port is protected by a firewall, so NULL, FIN and Xmas scans will only ever identify ports as being open|filtered, closed, or filtered. If a port is identified as filtered with one of these scans then it is usually because the target has responded with an ICMP unreachable packet.
That said, the goal here is, of course, firewall evasion. Many firewalls are configured to drop incoming TCP packets to blocked ports which have the SYN flag set (thus blocking new connection initiation requests). By sending requests which do not contain the SYN flag, we effectively bypass this kind of firewall. However, most modern IDS solutions can deal with these scan types.
The Xmas scan sends three flags: PSH, URG and FIN.
Answer: xmas
Many firewalls are configured to drop incoming TCP packets to blocked ports which have the SYN flag set. Since these three scans do not set a SYN flag they might evade the firewall.
Answer: Firewall Evasion
RFC 973 mandates that hosts respond to malformed packets with a RST TCP packet for close ports, and don’t respond at all for open ports. This is not always the case though, and particular Microsoft Windows (and a lot of Cisco network devices) are known to respond with a RST to any malformed TCP packet
Answer: Microsoft Windows
On connecting to a system, our first objective is to obtain a “map” of the network structure. In other words, we want to see which IP addresses contain active hosts, and which do not. Nmap can do this by running a “ping sweep”. What this means is that Nmap sends a ICMP packet to each possible IP address for the specified network. If it receives a response, it marks the address as being alive.
To perform a ping sweep, we use the -sn switch in conjunction with IP ranges.
Note: This scan is used to find the different machines on a network, and would normally be used before you start port/service scanning on individual hosts.
The right IP range to use is 172.16.0.0/16.
The /16 CIDR notation specifies the network range. It includes all IPs from 172.16.0.0 to 172.16.255.255 (a total of 65,536 possible addresses). Don’t forget nmap -sn of course.
Answer: nmap -sn 172.16.0.0/16
NSE stands for Nmap Scripting Language. NSE can greatly improve the functionality of Nmap with the use of scripts written in the Lua programming language.
There are many categories of scripts available, including:
A exhaustive list can be found here.
The NSE scrips are written in Lue.
Answer: Lua
Intrusive scripts are likely to affect the target and should not be run in a production environment.
Answer: intrusive
To run a specific script, we would use –script=<script-name>, for example:
nmap -- 80 --script=http-fileupload-exploiterMultiple scripts can be run simultaneously in this fashion by separating them by a comma.
The anwer can be found here:
https://nmap.org/nsedoc/scripts/ftp-anon.html
They are referring to maxlist, which is the maximum number of files to return in the directory listing. By default it is 20, or unlimited if verbosity is enabled. Use a negative number to disable the limit, or 0 to disable the listing entirely.
Answer: maxlist
We know how to run scripts, but how to find them? There are two options:
There are two ways to search for these installed scripts. One is by using the /usr/share/nmap/scripts/script.db file. Despite the extension, this isn’t actually a database so much as a formatted text file containing filenames and categories for each available script. Nmap uses this file to keep track of (and utilise) scripts for the scripting engine; however, we can also grep through it to look for scripts. For example:
grep "ftp" /usr/share/nmap/scripts/script.dbThe second way to search for scripts is quite simply to use the ls command in the scripts folder. For example, we could get the same results as in the previous screenshot by using:
ls -l /usr/share/nmap/scripts/*ftp*Let’s use the following command:
grep "ftp" /usr/share/nmap/scripts/script.dbYou will see a bunch of results but the one that makes sense is smb-os-discovery.nse.

Answer: smb-os-discovery.nse
Open the script by running:
cat /usr/share/nmap/scripts/smb-os-discovery.nseScroll a bit down in the script. Then you will find the answer:
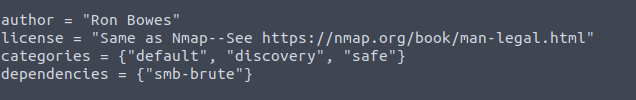
Answer: smb-brute
We have talked a lot about techniques for bypassing firewalls using stealthier scans. However, there is another common problem. Typical Windows hosts will due to its default firewall block all ICMP packets. This means that we can’t use ping on the network, and in addition nmap uses ICMP packets as well for scanning ports. Open ports will therefore not be detected.
We can bypass this problem by using the -Pn flag. This tells Nmap to avoid pinging hosts before
So, we need a way to get around this configuration. Fortunately Nmap provides an option for this: -Pn, which tells Nmap to not bother pinging the host before scanning it. This means that Nmap will always treat the target host(s) as being alive, effectively bypassing the ICMP block; however, it comes at the price of potentially taking a very long time to complete the scan (if the host really is dead then Nmap will still be checking and double checking every specified port).
Typical Windows hosts will often block all ICMP packets
Answer: ICMP
You can find the answer here:
https://nmap.org/book/man-bypass-firewalls-ids.html
—data-length <number> (Append random data to sent packets)
Normally Nmap sends minimalist packets containing only a header. So its TCP packets are generally 40 bytes and ICMP echo requests are just 28. Some UDP ports and IP protocols get a custom payload by default. This option tells Nmap to append the given number of random bytes to most of the packets it sends, and not to use any protocol-specific payloads. (Use –data-length 0 for no random or protocol-specific payloads. OS detection (-O) packets are not affected because accuracy there requires probe consistency, but most pinging and portscan packets support this. It slows things down a little, but can make a scan slightly less conspicuous.
Answer:–data-length
Before starting, boot up the machine attached to task 1.
Enter the following command:
ping <target ip>
We receive no response, so they answer is N.
Answer: N
You might remember that ports are run with -sX. To Xmas scan the first 999 ports we run the following command:
nmap <target ip> -sX -p 0-998We get the following result:

All 999 ports are open|filtered.
Answer: 999
The hint suggest use to run the scan with extra verbosity. Let’s run it with this command instead:
nmap <target ip> -sX -p 0-998 -vv
It seem that the ports are considered open|filtered because of receiving no-response.
Answer: No Response
We can use the -sS flag here, or leave it out as it is the default scan of nmap. Run the following command:
nmap 10.10.207.221 -sS -p 0-4999 -vv
There are 5 open ports.
Answer: 5
I am not going to cover Wireshark here.
But you can open Wireshark and start activating the capture of packets.

Make sure you add a display filter on the target ip address, otherwise you will have trouble seeing the traffic related to the port scan.
Then run a TCP Connect scan with the -sT flag.
nmap <target ip> -sT -p 80
As you can see, a three-way handshake is seen (SYN, SYN/ACK, ACK). The RST,ACK in the end is a connection refusal from the target server.
Answer: No answer needed
We are nearly done, let’s get this final question over with! As you might know, the ftp-anon script checks whether anonymous login is allowed to the target FTP server. This is a major vulnerability if possible.
Read more here:
https://nmap.org/nsedoc/scripts/ftp-anon.html
Run the following command to run the script on port 21 of the target server:
nmap 10.10.207.221 -p 21 --script=ftp-anon
As you can see, anonymous FTP login is allowed! To show that it is actually possible we can run:
ftp <target ip>Enter anonymous as username, and leave the password empty. You should see that you get logged on.

Answer: Y
We are done. Great job! I hope you learned as much as I did while writing this walkthrough of the TryHackMe: NMap room. NMap is an amazing tool which you will use for basicly every pentesting assignment. So master the tool and you will succeed 🙂

You can find my other walkthroughs here.
You are welcome to support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link: