Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the MITRE Room on TryHackMe. MITRE develops cybersecurity frameworks like ATT&CK, providing a shared knowledge base of adversary tactics and techniques to enhance threat detection, response, and defense strategies. They also run programs like CVE to track and manage vulnerabilities.
This room is part of the SOC Level 1 Path.

Room URL: https://tryhackme.com/r/room/mitre
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
Now, let’s move on!
MITRE is a non-proft corporation based in the US which provides projects/research on a variety of topics, including Cybersecurity. You might know MITRE from the list of Common Vulnerabilities and Exposures (CVEs). However, MITRE Corporation has provided much more to the cybersecurity community, specifically:
Let’s learn more about them!
Answer: No answer needed
The MITRE ATT&CK® framework is a globally accessible knowledge base documenting adversary tactics, techniques, and procedures (TTPs) observed in real-world scenarios. Initially focused solely on Windows, ATT&CK has since expanded to include platforms like macOS and Linux, supported by contributions from security researchers and threat intelligence reports.
ATT&CK is valuable for both blue teamers and red teamers. Blue teamers use it to enhance threat detection and defensive coverage, while red teamers use it to plan simulations. The framework includes the ATT&CK Matrix, organizing techniques into 14 categories aligned with the Cyber Attack Lifecycle (e.g., Initial Access, Execution, Persistence). Techniques like Phishing include sub-techniques, all detailed with descriptions, examples, and mitigations.

If you haven’t done so, navigate to the ATT&CK® website.
Additionally, the ATT&CK Navigator allows users to interactively explore the matrix, map threat groups to their tactics and techniques, and visualize defensive coverage or attack plans. This versatility makes ATT&CK an essential tool for understanding and addressing cyber threats. You can find it here.
Go ahead and have a look at the matrix:
https://attack.mitre.org/matrices/enterprise
You should be able to find the technique in the Defense Evasion column, and you can read more here:
https://attack.mitre.org/techniques/T1564
Answer: Defense Evasion
Have another look at the Matrix. You can find this technique underneath Persistence. And finding it will bring you to the following page:
https://attack.mitre.org/techniques/T1136
You can find the answer in the URL, or simply look at the page:
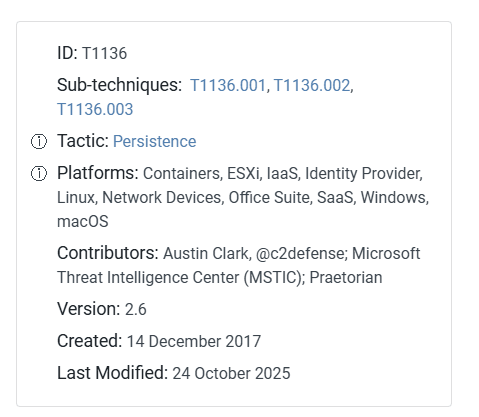
Answer: T1136
| Role | Goal | How They Use ATT&CK |
|---|---|---|
| CTI Teams | Collect & analyze threat info | Map threat actor behavior to TTPs for actionable profiles |
| SOC Analysts | Investigate & triage alerts | Link activity to tactics/techniques for context & prioritization |
| Detection Engineers | Improve detection systems | Map SIEM/EDR rules to ATT&CK for stronger detection |
| Incident Responders | Investigate incidents | Map timelines to ATT&CK tactics for attack visualization |
| Red & Purple Teams | Test & improve defenses | Build emulation plans aligned with known adversary techniques |
Let’s say your organization has been the victim of an attack. In a post-incident scenario, it is crucial to analyze how the attack unfolded and map each stage in a structured format. This will allow your team to better prepare for future campaigns targeting your organization.
The group Mustang Panda (G0129) has been mapped to a variety of ATT&CK techniques based on its years of attacking government entities, non-profits, and NGOs. Below, you can see that Mustang Panda prefers phishing techniques for initial access, persists via scheduled tasks, obfuscates files to evade defenses, and uses an ingress tool transfer for command and control. For the questions in this task, you will analyze Mustang Panda’s dedicated page and associated matrix using the ATT&CK Navigator.
Go ahead and look at the earlier linked page: https://attack.mitre.org/groups/G0129/
Here it mentions that:
Mustang Panda is a China-based cyber espionage threat actor that has been conducting operations since at least 2012. Mustang Panda has been known to use tailored phishing lures and decoy documents to deliver malicious payloads. Mustang Panda has targeted government, diplomatic, and non-governmental organizations, including think tanks, religious institutions, and research entities, across the United States, Europe, and Asia, with notable activity in Russia, Mongolia, Myanmar, Pakistan, and Vietnam. [1][2][3][4][5][6][7][8][9][10][11][12][13]
Hence, the answer is China.
Answer: China
Look at the matrix earlier mentioned on the Mustang Panda’s dedicated page:
Go ahead and look up the Reconnaissance column, which is all the way to the left. Here there is one technique highlighted which is related to phishing:
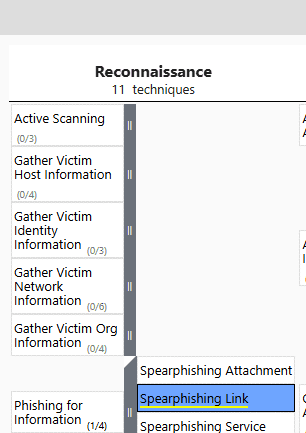
If you hover over it you will see that the technique has number T1598.
Answer: T1598
Strange enough, token manipulation is not highlighted on the matrix we looked at earlier. But let’s have a ook at the group’s page:
https://attack.mitre.org/groups/G0129
Here we can see that a software they use is called Cobalt Strike, which can be used for access token manippulation:
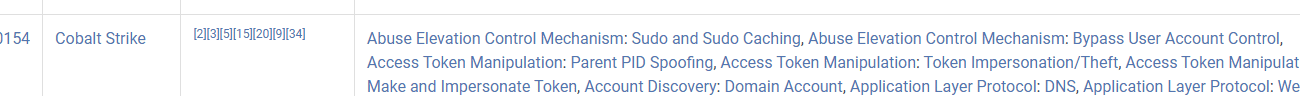
Answer: Cobalt Strike
In the previous task, we explored how organizations and teams utilize Cyber Threat Intelligence (CTI) to understand adversary behavior and inform defense strategies by mapping intelligence to the ATT&CK framework. You also gained some experience using the Navigator to analyze a group’s TTPs. Now, you’ll use your newly gained knowledge to research threat groups that might target your organization.
You are a security analyst in the aviation sector, and your organization is migrating its infrastructure to the cloud. Your task is to use ATT&CK to gather intelligence on APT groups known to target this sector, identify their tactics and techniques, and assess any potential gaps in your defensive coverage.
You’ll use the Groups section on the ATT&CK website to find an appropriate group and analyze its behavior using the Navigator layer and technique pages.
For this you can look at the earlier linked Groups section. Here you can find a list of APT groups. I simply searched on the page for “aviation” and ended up finding 6 results. One of the is APT33, which is a suspected Iranian threat group that has been active since at least 2013.

Answer: APT33
Let’s have a look at the APT33 group page:
https://attack.mitre.org/groups/G0064
If you search for “office 365”, you will find the technique called “Cloud Accounts”, which refers to the fact that APT33 has used compromised Office 365 accounts in tandem with Ruler in an attempt to gain control of endpoints.

Answer: Cloud Accounts
Click on the technique link to go to the following page:
https://attack.mitre.org/techniques/T1078/004
Underneath Procedure Examples it actually mentions the same line again:
APT33 has used compromised Office 365 accounts in tandem with Ruler in an attempt to gain control of endpoints.[7]
Ruler is the answer!
Answer: Ruler
Let’s keep look at the technique page: https://attack.mitre.org/techniques/T1078/004/
Underneath Mitigations, it says:
| User Account Management | Periodically review user accounts and remove those that are inactive or unnecessary. Limit the ability for user accounts to create additional accounts. |
Answer: User Account Management
Right underneath the Mitigations table, there is a Detection Strategy table, which currently has one entry:
Answer: DET0546
MITRE defines the Cyber Analytics Repository (CAR) as “a knowledge base of analytics developed by MITRE based on the MITRE ATT&CK adversary model. CAR defines a data model that is leveraged in its pseudocode representations, but also includes implementations directly targeted at specific tools (e.g., Splunk, EQL) in its analytics. With respect to coverage, CAR is focused on providing a set of validated and well-explained analytics, in particular with regard to their operating theory and rationale.”
This all sounds a bit complex, so let’s break it down. CAR is a collection of ready-made detection analytics built around ATT&CK. Each analytic describes how to detect an adversary’s behavior. This is key because it allows you to identify the patterns you should look for as a defender. CAR also provides example queries for common industry tools such as Splunk, so you, as a defender, can translate ATT&CK TTPs into real detections.
Let’s dive in and get some hands-on experience with CAR. We will begin by examining CAR-2020-09-001: Scheduled Task – File Access. Upon visiting the page, we are given a description of the analytics and references to the associated ATT&CK tactics and techniques.
In the Implementations section, you are provided with Pseudocode, a Splunk query, and a LogPoint search as examples of how an analyst may filter for this technique using their organization’s Security Information and Event Management (SIEM) platform. Pseudocode is a plain, human-readable way to describe a set of instructions or algorithms that a program or system will perform. Note that not every analytic within CAR will have the same implementation examples. Some analytics even include Unit Tests, which an analyst can use to validate whether the analytic works as intended.
CAR also has its own ATT&CK Navigator layer in which techniques are mapped to a matrix similar to what you saw previously when investigating groups. You will utilize the CAR Analytics List and matrix for the questions in this task.
This one is easy. Open up the page, and you will see the following table:
| Technique | Subtechnique(s) | Tactic(s) | Level of Coverage |
|---|---|---|---|
| File and Directory Permissions Modification | Windows File and Directory Permissions Modification, Linux and Mac File and Directory Permissions Modification | Defense Evasion | Moderate |
On the third column it says Defense Evasion.
Answer: Defense Evasion
Go ahead and open up the CAR Analytics list:
https://car.mitre.org/analytics
Search for Access Permission Modification, and you will be lead to the following page:
https://car.mitre.org/analytics/CAR-2019-07-001
On the right side of the page you can find the following info, including the analytic type:
Submission Date: 2019/07/08
Update Date:
Information Domain: Host
Data Subtypes: File
Analytic Type: Situational Awareness
Applicable Platforms: Windows, Linux, macOS
Contributors: Meric Degirmenci, MITRE
Answer: Situational Awareness
With MITRE ATT&CK, you learn how attacks happen, but with MITRE D3FEND, you discover how to stop them.
D3FEND (Detection, Denial, and Disruption Framework Empowering Network Defense) is a structured framework that maps out defensive techniques and establishes a common language for describing how security controls work. D3FEND comes with its own matrix, which is broken down into seven tactics, each with its associated techniques and IDs.
For example, the Credential Rotation D3-CRO technique emphasizes the regular rotation of passwords to prevent attackers from reusing stolen credentials. D3FEND explains how this defense works, what to consider when implementing it, and how it relates to specific digital artifacts and ATT&CK techniques, helping you see both perspectives: the attacker’s move and the defender’s countermeasure.

Go to the linked page in the question. In the bottom you will find a table of sub-techniques. One of them is as follows:
| – User Geolocation Logon Pattern Analysis | D3-UGLPA | Monitoring geolocation data of user logon attempts and comparing it to a baseline user behavior profile to identify anomalies in logon location. |
Answer: User Geolocation Logon Pattern Analysis
Click on the sub-technique:
https://d3fend.mitre.org/technique/d3f:UserGeolocationLogonPatternAnalysis
Here you can read the following:
This defensive technique is related to specific digital artifacts. Click the artifact node for more information.
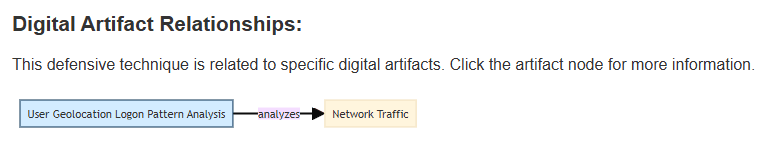
The text in the yellow box (the artifact) is the answer.
Answer: Network Traffic
Beyond the frameworks and tools we have discussed previously, MITRE offers several other projects designed to help cyber security professionals strengthen their skills, test their defenses, and outsmart attackers. In this task, we will briefly explore these tools and how they can support your growth in the field.
MITRE’s Adversary Emulation Library, primarily maintained and contributed to by The Center for Threat Informed Defense (CTID), is a free resource of adversary emulation plans. The library currently contains several emulations that mimic real-world attacks by known threat groups. The emulation plans are a step-by-step guide on how to mimic the specific threat group.
Caldera is an automated adversary emulation tool designed to help security teams test and enhance their defenses. It provides the ability to simulate real-world attacker behavior utilizing the ATT&CK framework. This allows defenders to evaluate detection methods and practice incident response in a controlled environment. Caldera supports offensive and defensive operations, making it a powerful tool for red and blue team exercises.
AADAPT (Adversarial Actions in Digital Asset Payment Technologies) is a newly released knowledge base that includes its own matrix, covering adversary tactics and techniques related to digital asset management systems. AADAPT follows a similar structure to the ATT&CK Framework we covered previously and aims to help defenders understand and mitigate threats targeting blockchain networks, smart contracts, digital wallets, and other digital asset technologies.
ATLAS (Adversarial Threat Landscape for Artificial-Intelligence Systems) is a knowledge base and framework that includes a matrix, focusing on threats targeting artificial intelligence and machine learning systems. It documents real-world attack techniques, vulnerabilities, and mitigations specific to AI technology.
So, if you read the text you know that AADAPT is similar in structure to the ATT&CK framework, but focuses on blockchain technologies.
All you have to do here is visit the hyperlink, and on the right side you will see the technique ID.
Answer: ADT3025
Another easy one. Visit the page and on your right you will find the answer:
Answer: Defense Evasion
In this room, you explored the tools and resources that MITRE has provided to the security community. The goal is to introduce you to these resources and provide you with a foundational understanding of their uses. Many vendors of security products and security teams worldwide consider these resources invaluable in their day-to-day efforts to thwart attackers. The more information we have as security professionals, the better equipped we are to fight back!
Answer: No answer needed

It was amazing to learn about the different tools provided by MITRE. They really help us understand cyber threats and how to mitigate these. Great job on following along. Happy hacking!
Find more of my TryHackMe SOC Level 1 Path walkthroughs here.
Find more of my walkthroughs here.
You are welcome to comment this post, and please share with friends.mal
I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] TryHackMe: MITRE Walkthrough (SOC Level 1) […]