Jasper Alblas
Jasper Alblas
Mastering Data & Cybersec
Welcome to this walkthrough of the SOC L1 Alert Reporting room on TryHackMe. In the last room we learned about triaging alerts. In this room we discuss about another important element related to alert, and that is how to properly report, escalate and communicate about high-risk SOC alerts.

Room URL:
https://tryhackme.com/room/socl1alertreporting
I am making these walkthroughs to keep myself motivated to learn cyber security, and ensure that I remember the knowledge gained by these challenges on HTB and THM. Join me on learning cyber security. I will try and explain concepts as I go, to differentiate myself from other walkthroughs.
During or after alert triage, L1 analysts may be uncertain about how to classify the alert, requiring senior support or information from the system owner. Also, L1 may deal with real cyberattacks and breaches that need immediate attention and remediation actions. This room covers these cases by introducing three new terms: alert reporting, escalation, and communication.
Continue your journey in the SOC dashboard! This time you will need it to write professional reports and practice in escalating the alerts. Open the attached website in a separate window by clicking on the SOC dashboard link below and move on to the next task!
Answer: No answer needed
So, you’ve triaged an alert — what happens next? Your work as an L1 analyst doesn’t just end when you mark an alert as Closed. Each investigation plays a crucial role in helping the SOC detect, respond to, and ultimately prevent cyberattacks.
In most cases, L1 analysts handle the majority of alerts themselves. However, some alerts — especially confirmed or complex True Positives — need to be passed on to L2 analysts for deeper analysis and remediation. This process relies on three essential steps:
Before escalating or closing an alert, you may need to document your findings in more detail than just a short comment. A thorough report should include your investigation steps, collected evidence, and conclusions. This documentation is vital for transparency and for helping others understand your analysis later.
When an alert turns out to be a real threat requiring further action, it must be escalated to an L2 analyst. Your detailed report ensures they can quickly pick up where you left off, saving valuable time and helping them focus on mitigation instead of starting from scratch.
During or after triage, you might also need to coordinate with other departments – asking IT to verify privilege changes, HR to confirm employee details, or management for awareness. Clear communication ensures that the entire organization stays aligned during an incident.
By effectively reporting, escalating, and communicating, SOC analysts turn raw alerts into actionable intelligence — creating a seamless flow from detection to response.
When an alert turns out to be a real threat requiring further action, it must be escalated to an L2 analyst
Answer: alert escalation
We call this alert reporting.
Answer: alert reporting
As an L1 analyst, writing a short but structured report is more than busywork — it’s a force multiplier for the whole SOC. Good L1 reports:
Think like the person who will pick up your work (L2, DFIR, IT). Make it easy for them by answering the Five Ws:
Keep the report short, factual, and evidence-backed — include key log snippets or fields if available. A clear Five Ws report speeds up escalation, preserves institutional memory, and helps you become a stronger analyst.
Go ahead and visit the SOC dashboard. You will see 5 alerts, of which one is called Sensitive Document Share to External. That seems right! Open the details by pressing the arrow on the far right.
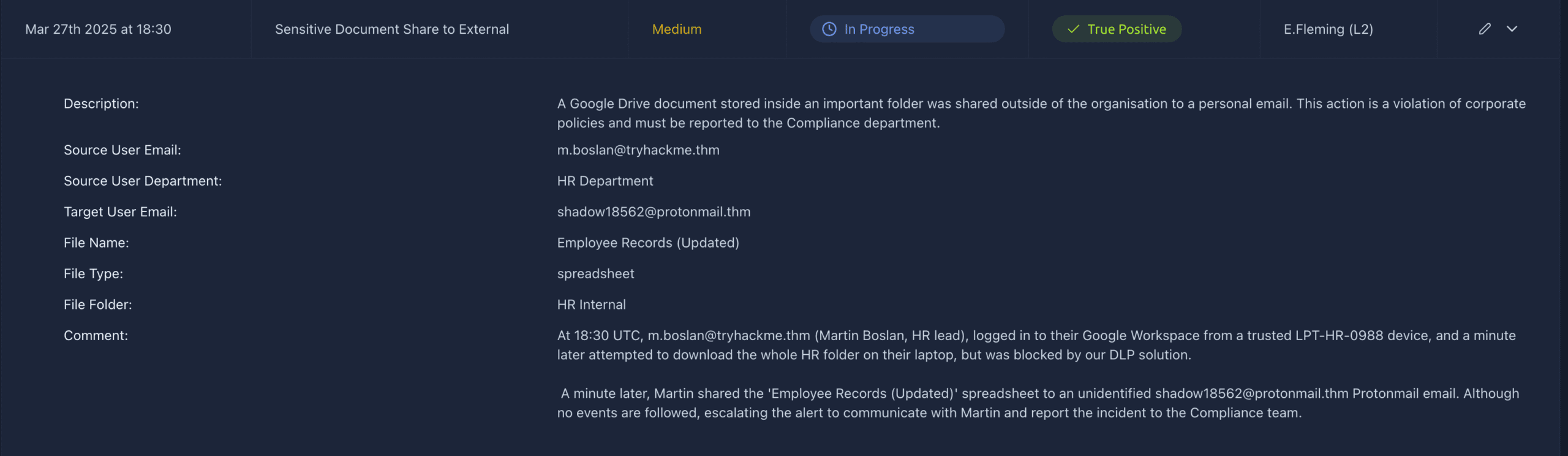
The answer is found under source user email, which in this case is m.boslan@tryhackme.thm.
Answer: m.boslan@tryhackme.thm
Look at the two new alerts. One of them is called Email marked as Phishing after Delivery. Open the details:
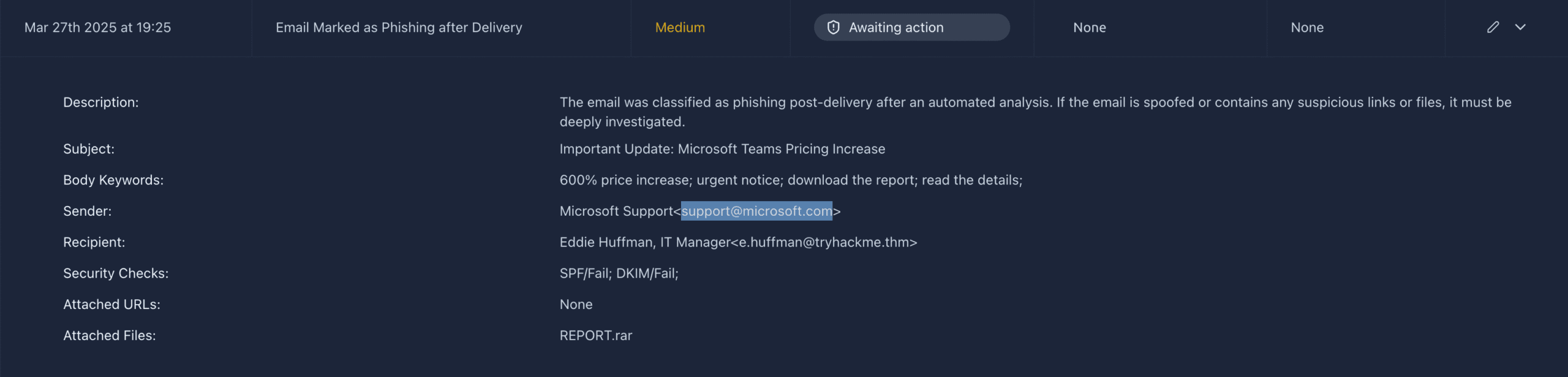
The email address is found under Sender, in this case support@microsoft.com.
Answer: support@microsoft.com
This is the same alert as the one we have open. Study it a bit more to understand the activity. To be honest, I had to research what SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail) meant. Both tests test whether the sender is authorised to send from the Microsoft domain. Both tests fail, meaning that this is a sign of spoofing. In addition, there are urgency-based social engineering triggers (“urgent notice”, “price increase”). Finally, there is a archive attached, another red flag.
I made the following report:
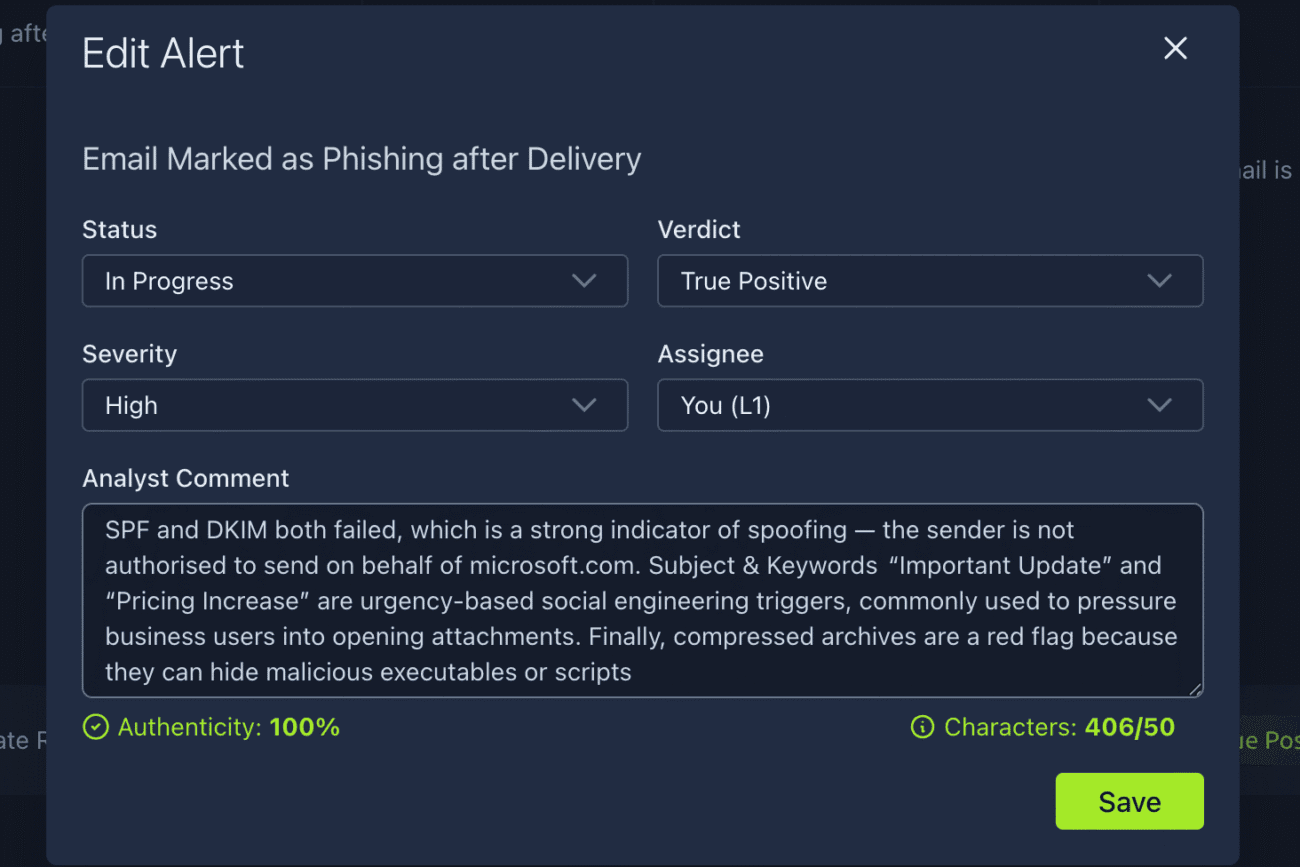
Save the report and you should see a flag.
Answer: THM{nice_attempt_faking_microsoft_support}
After you have made a verdict and written your alert report, decide whether to escalate the alert to L2. The answer may differ between teams, but these recommendations generally apply.
Escalate the alert to L2 if any of the following apply:
Example: L1 escalates a phishing alert to L2, and L2 rotates the user’s credentials.
L2 will receive the ticket from you, read your report, and contact you if they need clarification. Once clear, L2 typically:
It is acceptable for L1 to request senior support when something is unclear. Especially during early months, it’s better to discuss the alert and clarify SOC procedures than to close an alert you don’t understand.
Simply look at the two alerts that are in progress. They are assigned to E.Fleming (L2).
Answer: E.Fleming
Go ahead and go back to the alert from the previous task. Make sure you set it to in progress and assign it to E.Fleming.
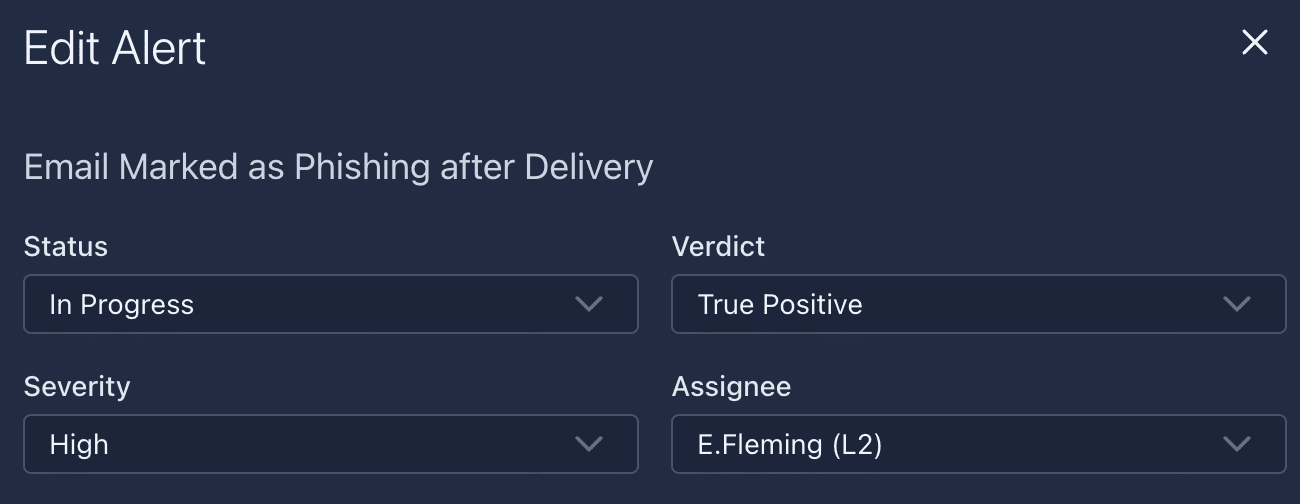
A flag should show up.
Answer: THM{good_job_escalating_your_first_alert}
Time to look at the final alert:
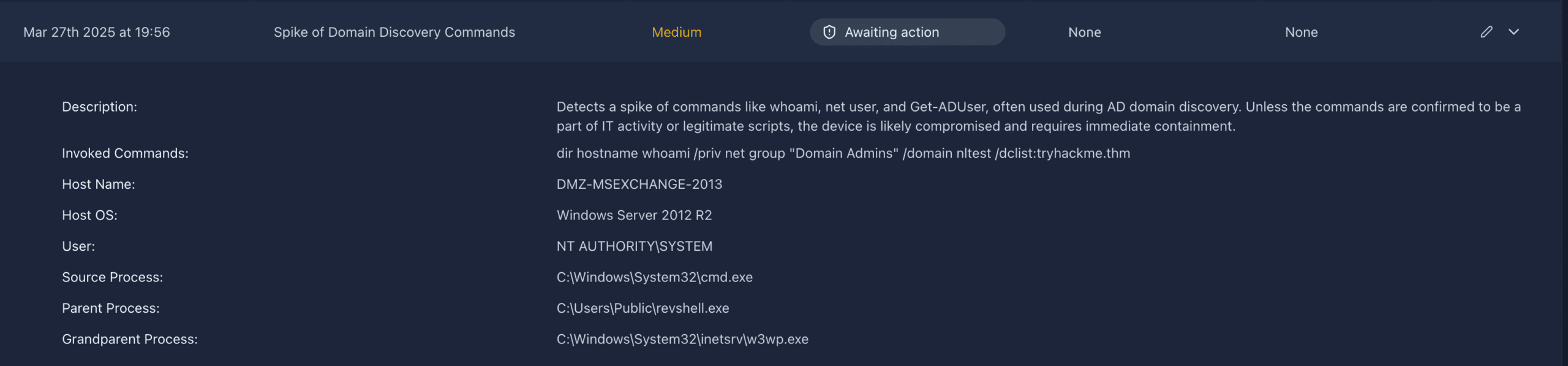
There are a few to to notice here. The invoked commands seem to related to Active Directory reconnaissance:whoami, net user, Get-ADUser, nltest, net group "Domain Admins" /domain
These are classic enumeration commands used by attackers after gaining a foothold.
Secondly, the parent process is revshell.exe, which is a very suspicous name and seems to indicate a reverse shell executable. It is also located in the Public folder, which is a common location for attack file drops.
Thirdly, the user
NT AUTHORITY\SYSTEM is running at the highest privilege level , meaning the attacker has achieved privilege escalation.
Finally, the host is a mail server, which means the attacker has probably gained access through this host as they are commonly internet-facing.
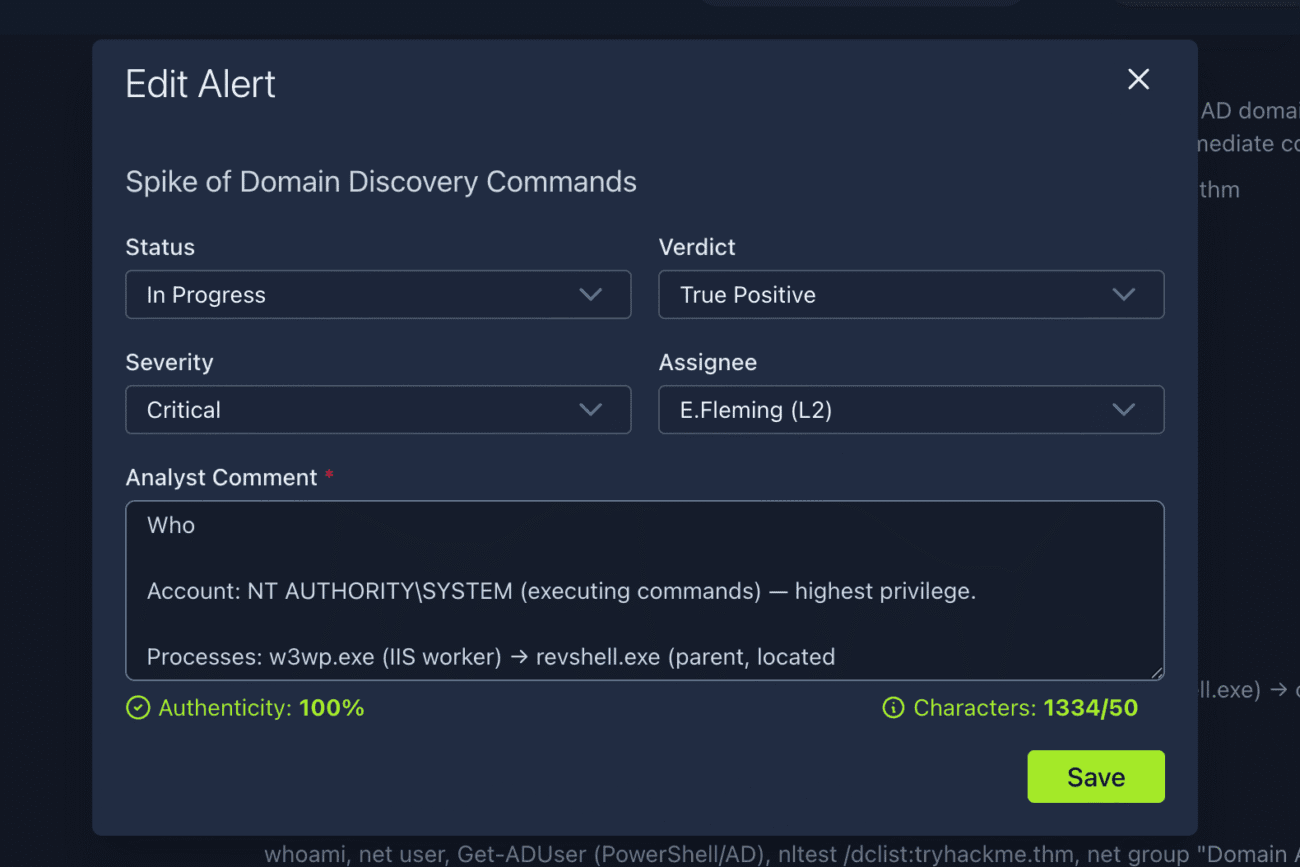
I used the following comment:
Who
Account: NT AUTHORITY\SYSTEM (executing commands) — highest privilege.
Processes: w3wp.exe (IIS worker) → revshell.exe (parent, located C:\Users\Public\revshell.exe) → cmd.exe (source process executing commands).
What
Observed commands indicative of AD/domain discovery and privilege enumeration:
whoami, net user, Get-ADUser (PowerShell/AD), nltest /dclist:tryhackme.thm, net group “Domain Admins” /domain, plus dir and hostname.
When
Detection occurred when the SIEM raised this alert (use the SIEM event/ticket timestamp).
Action for L1: capture and record the exact SIEM event timestamp and related log timestamps (IIS, Windows Security, Sysmon if available) as part of evidence collection.
Where
Host: DMZ-MSEXCHANGE-2013 (Windows Server 2012 R2) — a mail server in the DMZ (likely internet-facing).
Files/process paths: C:\Users\Public\revshell.exe, C:\Windows\System32\cmd.exe, C:\Windows\System32\inetsrv\w3wp.exe.
Why / How (likely)
Likely chain: attacker exploited the mail/Exchange-facing service (IIS) → uploaded or executed a web shell / reverse shell (revshell.exe) → spawned cmd.exe running AD enumeration commands as SYSTEM.
Purpose of commands: enumeration of domain users, domain controllers, and privileged groups (preparation for credential theft, lateral movement, or privilege escalation tasks).
Answer: THM{looks_like_webshell_via_old_exchange}
The escalation and reporting topics should sound straightforward and logical to you. However, as always, it is easier said than done. You should be prepared for unexpected situations and know how to act in critical cases.
In the best scenario, your SOC team has established Crisis Communication procedures — guides and processes designed to help you and your teammates resolve such issues efficiently.
If not, review the following example cases and be ready to handle them effectively.
1. You need to escalate an urgent, critical alert, but L2 is unavailable and does not respond for 30 minutes.
Make sure you know where to find emergency contacts. First, try to call L2 directly. If there is no response, contact L3, and finally your manager.
2. The alert about a Slack or Teams account compromise requires you to validate the login with the affected user.
Do not contact the user through the potentially breached chat. Instead, use an alternative communication method, such as a phone call.
3. You receive an overwhelming number of alerts within a short period, some of which are critical.
Prioritize the alerts according to your workflow, but immediately inform the L2 on shift about the situation.
4. After a few days, you realize that you misclassified an alert and likely missed a malicious action.
Contact your L2 immediately and explain your concerns. Remember that threat actors can stay silent for weeks before causing any impact.
5. You cannot complete the alert triage because SIEM logs are not parsed correctly or are not searchable.
Do not skip the alert. Investigate as much as possible and report the issue to your L2 on shift or the SOC engineer.
No, follow the correct procedure if possible. Triage to a L2 first.
Answer: nay
Yes. If you think you missed a attack, contact your L2. Better safe than sorry!
Answer: yea
Great job learning three important SOC skills: alert reporting, escalation, and communication. These skills are essential for any L1 analysts: Alert reporting helps to preserve and provide activity context for L2, escalation ensures threats are remediated in time, and communication makes the coordination between SOC and other departments clear and effective.
Answer: No answer needed
Congratulations on completing SOC L1 Alert Reporting. I actually really liked this room, as we really got to get a feeling of how proper SOC work is done. Calmly investigate alerts in the proper order, make notes, and triage if needed!
Come back soon for more walkthroughs of rooms on TryHackMe and HackTheBox, and other Cybersecurity discussions.
Find my SOC Level 1 Path walkthroughs here.
Find my other walkthroughs here.
You are welcome to comment on this post, or share my post with friends.I would be even more grateful if you support me by buying me a cup of coffee:

I learned a lot through HackTheBox’s Academy. If you want to sign up, you can get extra cubes, and support me in the process, if you use the following link:
[…] SOC L1 Alert Reporting […]